Cryptography Reference
In-Depth Information
100
80
60
40
20
using 32768 keystreams
0
1
10
100
1000
time in minutes for the last phase of the attack (logscaled)
Fig. 4.
Time to completion of the attack using a single FPGA and 2
32
equations
The runtime of these two phases is only affected by the rate of the keystream
recovery process and the computing power available.
In the third and last phase, the adversary uses the frequency tables generated
in phase two to search for the correct key. He uses a PC which generates the most
likely sub key spaces as described in Section 4 and transfers them to a single
or multiple FPGAs connected via a serial line or other interfaces. The time for
generating the sub key spaces is negligible compared to the time consumed by
the FPGAs to check the sub key space, so that many FPGAs can be supplied
by a single PC.
Figure 4 shows the time to the completion of the last attack phase, using
just a single Xilinx Spartan-3E 1200 (XC3S1200E) FPGA using 2
15
keystreams.
About 20% of our experiments completed within one hour. The next 20% of our
experiments needed up to one day to complete. The remaining 60% needed more
than a day to complete. Please note that doubling the number of FPGAs used
reduces the total time for the last phase by half and the attack scales almost
perfectly when the number of available FPGAs is increased.
References
1. Alcatel. Data ciphering device. U.S. Patent 5,608,802 (1994)
2. Lucks, S., Schuler, A., Tews, E., Weinmann, R.P., Wenzel, M.: Attacks on the
DECT authentication mechanisms. In: Topics in Cryptology-CT-RSA 2009, pp.
48-65 (2009)
3. Molter, H.G., Ogata, K., Tews, E., Weinmann, R.P.: An E
cient FPGA Implemen-
tation for an DECT Brute-Force Attacking Scenario. In: 2009 Fifth International
Conference on Wireless and Mobile Communications, pp. 82-86. IEEE, Los Alami-
tos (2009)
4. Nohl, K., Tews, E., Weinmann, R.P.: Cryptanalysis of the DECT Standard Cipher
(February 2010)






































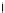








































Search WWH ::

Custom Search