Biomedical Engineering Reference
In-Depth Information
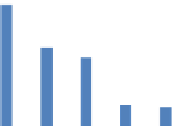
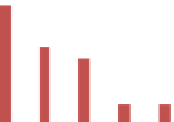
Table 1 A performance
matrix based on execution
time
Execution time (ms)
Processor
Recent architecture
Proposed architecture
Pentium 4
15,170
14,504
Dual core
9,876
9,408
Core 2 duo
8,660
8,142
i3
2,865
2,448
i5
2,504
2,308
Chart 1 A performance-
based chart
20000
15000
RECENT
ARCHITECTURE
10000
5000
PROPOSED
ARCHITECTURE
0
Performance Evaluation
In order to evaluate the performance of the proposed architecture, we first
implement both the security protocol architecture's using Java 1.6 and then
execute both architecture implementation codes over a number of hardware plat-
form (processors) under ideal conditions. The common data set given as an input
to both the architecture implementation in order to get the most accurate execution
time as possible.
Table
1
contains the average execution time of both the architecture implementation.
The average execution time is obtained by first making 1,000 hits to the security
architecture implementation and then by dividing the total execution time we get faster
the execution of architecture implementation by 1,000. The same methodology adopted
in the software companies in order to know the performance of the code (Chart
1
).
However, the selection of the programming language for implementing both the
security protocol architecture is obvious Java programming language because of
two simple reasons:
1. Java is platform-independent language, i.e., we can develop the code of the
proposed architecture in it and then makes it run on any platform. The devel-
oped code will be platform independent which in turn increases the domain of
its application in a variety of fields such as use of proposed hybrid security
protocol in Mobile Adhoc network (MANET) also apart from E-commerce and
M-commerce transactions [
12
].











Search WWH ::

Custom Search