Biomedical Engineering Reference
In-Depth Information
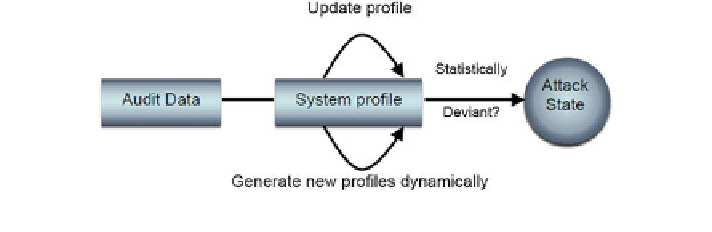
Fig. 2
A typical anomaly detection system
an undesired connection. All connections are modeled as binary strings and there
is a set of known good and bad connections, which is used to train and evaluate the
algorithm. To build the AIS, random binary strings are created called detectors.
These detectors then undergo a maturation phase where they are presented with
good, i.e., self, connections. If they match any of these they are eliminated
otherwise they become mature, but not activated. If during their further lifetime
these mature detectors match anything else, exceeding a certain threshold value,
they become activated. This is then reported to a human operator who decides
whether there is a true anomaly. If so the detectors are promoted to memory
detectors with an indefinite life span and minimum activation threshold. Thus, this
is similar to the secondary response in the natural immune system, for instance
after immunization.
An approach such as the above is known in AIS as negative selection as only
those detectors (antibodies) that do not match live on. It is thought that T cells
mature in similar fashion in the thymus such that only those survive and mature
that does not match any self cells after a certain amount of time.
An alternative approach to negative selection is that of positive selection as
used for instance by Forrest et al. [14] and by Somayaji and Forrest [16]. These
systems are a reversal of the negative selection algorithm described above with the
difference that detectors for self are evolved. From a performance point of view
there are advantages and disadvantages for both methods. A suspect non-self string
would have to be compared with all self-detectors to establish that it is non-self,
whilst with negative selection the first matching detector would stop the com-
parison. On the other hand, for a self-string this is reversed giving positive
selection the upper hand. Thus, performance depends on the self to non-self ratio,
which should generally favor positive selection.
However, there is another difference between the two approaches: the nature of
false alarms. With negative selection inadequate detectors will result in false
negatives (missed intrusions) whilst with positive selection there will be false
positives (false alarms). The preference between the two in this case is likely to be
problem specific.
What could such danger signals be? They should show up after limited infec-
tion to minimize damage and hence have to be quickly and automatically mea-
surable. Suitable signals could include:
Search WWH ::

Custom Search