Cryptography Reference
In-Depth Information
4. There is no protection for integrity of the source and target addresses.
Diagram 9.1 WEP Encryption
k
RC4
ICV
IV
v
←−−−−
m
ICV
(
m
)
R
(
k,v
)
v
(
m
,
ICV
(
m
))
−−−−→
⊕
P
C
−−−−→
(
v
,
C
)
C
−−−−→
Diagram 9.2 WEP Decryption
k
RC4
ICV
→
ICV
(
m
)
↑
Compare
↓
−−−−→
v
m
P
ICV
(
m
)
R
(
k
,
v
)
⊕
C
−−−−→
P
C
−−−−→
→
ICV
(
m
)
WEP Replacement
The TGi proposed standard, 802.11i, was ratified by IEEE in June of 2004.
Before the long-awaited ratification by the TGi, there was a transitional speci-
fication called
Wi-Fi Protected Access
(WPA) which was adopted by the Wi-Fi
Alliance in November of 2002, largely to respond to the impatience over the long
gestation period for the ratification of 802.11i. It was designed to be deployed
as a software upgrade to existing WLAN hardware. However, WPA is not an
802.11 standard. Rather, it complements and is based on 802.11i, a strongele-
ment of which is the
Robust Security Network
(RSN). Since WPA is essentially
a subset of RSN, we look at it first.
Summary of RSN Features
1. AES is employed with a 128-bit key, but supports key lengths up to 256
bits. Although RSN does
not
introduce new hardware, it will be affected
by the fact that any RSN-compliant device will be required to support







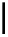
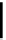




























Search WWH ::

Custom Search