Cryptography Reference
In-Depth Information
In Diagrams 8.10 and 8.11, which conclude the discussions for this section, we
illustrate both clear signingand the combination of envelopingand signingwith
S/MIME. We have not discussed the actual certificate processingwith S/MIME
since this is essentially a facet of the PKI structures discussed in Section 6.2, to
which we refer the reader for a reminder of this mechanism.
Diagram 8.10 Clear Signed S/MIME Message
I
e
A
C
(
A
)
I
RSA
d
A
d
A
(
m
)
(
I
e
A
,
C
(
A
)
,
I
RSA
,
d
A
(
m
)
d
A
(
h
(
m
))
,
m
)=
CSM
MIME
Body
m
−−−−→
d
A
(
m
)
−−−−−→
CSM
m
in the clear
Base
64
Encode
−
CSM
64
←−−−−−−−−−−−−−−−−−−−−−−−−−−−−−−
(
m
,
CSM
64
)
OUTPUT
Diagram 8.11 Signed and Enveloped S/MIME Message
m
−−−−→
signs m
SDM
ALICE
Envelopes SDM
→
OUTPUT
−−−−→
———————
OR———————
m
−−−−→
ED
−−−−→
ALICE
Envelopes m
signs ED
→
OUTPUT
In the next section, we look at IP-level security since there are security
issues that cross the protocol layers (see Section 5.7). Such applications-specific
security schemes such as PGP and S/MIME, for example, do not address issues
where a particular network might want to restrict ingress and egress of data to
and from its site. We will see that IPSec (initially mentioned on page 137 in
connection with CTR mode), provides security at the network layer, that layer
between the bottom physical layer and the next layer up, the transport layer.
Recall that we already discussed SSL in depth in Section 5.7, which deals with
security at the transport layer. Thus, the next section deals with yet another
aspect of protocol level security for our Internet activities, such as remote logins,
file transfer, WWW access, as well as e-mail and more.


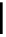
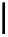
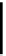

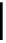





























Search WWH ::

Custom Search