Cryptography Reference
In-Depth Information
Diagram 8.5 PGP Message Components
ASCII Converted
Session Key
I
e
B
e
B
(
k
)
E
k
Encrypted
ZIP-Compressed
Signature
I
e
A
t
A
d
A
(
m
,
h
(
t
A
,
m
))
L
1
,
L
2
Message Data
F
m
t
m
m
The next topic is a fundamental feature of PGP and is a mechanism for an
individual user to communicate with entities it knows, securely, and eJciently.
From the above, it can be seen that the key identities,
I
e
A
and
I
e
B
, for Alice
and Bob, respectively, provide authentication and confidentiality. Bob's public
and private keys are stored securely at his computer alongwith public keys of
others, such as Alice, with whom he communicates. PGP uses data structures to
store them, called
public key rings
and
private key rings
. We now describe each
of these in turn, and delineate the schemes by which private keys are securely
maintained.
Key Rings
The private key ringis stored only on Alice's computer, which stores the
RSA key pairs owned by her, and is accessible only to Alice. In the private key
ring, each entry for an entity has the following fields (but typically she will only
have one entry, namely, her own public/private key pair).
Private Key Ring Individual Field Entry
1.
Timestamp
:
t
A
, the creation time of (
e
A
,d
A
).
2.
Key ID
:
I
e
A
(mod 2
64
).











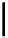


















Search WWH ::

Custom Search