Cryptography Reference
In-Depth Information
b
5
b
4
b
3
b
2
b
1
b
0
b
6
b
5
b
4
b
3
b
2
b
1
b
0
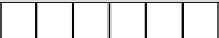
FIGURE 2.1: LFSR: one step evolution
cal development for a long time, leading to elegant results in the area of linear
complexity [62].
A nonlinear combiner model takes n LFSRs of different lengths (may be
pairwise co-prime). They are initialized with non-zero seeds. In each clock, n-
many outputs from the LFSRs are taken and fed as n-inputs to an n-variable
Boolean function. Some memory element may optionally be added.
For nonlinear filter-generator model, n-many outputs from different loca-
tions of the LFSR are fed as n-inputs to an n-variable Boolean function. Here
too, some memory element may be optionally added. The Boolean function
and memory together form a Finite State Machine.
We now mention a few recent state-of-the-art hardware stream ciphers.
E
0
is a stream cipher used in the Bluetooth protocol for link encryption. It
uses 4 LFSRs of lengths 25, 31, 33 and 39 bits and one FSM to combine their
outputs. Several vulnerabilities [53,60,69,98] have already been discovered for
this cipher. A5/1 is a stream cipher used to provide over-the-air voice privacy
in the GSM cellular telephone standard. A5/1 consists of three short binary
LFSRs of length 19, 22, 23 denoted by R1, R2, R3 respectively. The LFSRs are
clocked in an irregular fashion. The works [13,20,41,59] constitute important
attacks against this cipher. Grain [66] is a stream cipher primitive that is
designed to be accommodated in low end hardware. It contains three main
building blocks, namely a linear feedback shift register (LFSR), a nonlinear
feedback shift register (NFSR), both of 80-bit size, and a filter function. Given
certain attacks on Grain [115], a new cipher in a similar direction, called Grain-
128 is proposed in [67]. In the hardware implementation of the Grain family of
stream ciphers, the gate count is very low and it is expected that these ciphers
can be accommodated in very low end hardwares, even in RFID tags. SNOW
3G is chosen as the stream cipher for the 3GPP encryption algorithms [43]. It
is an LFSR based stream cipher with 32-bit words with a 128-bit key. Except
the fault analysis [35], no other attacks on this cipher are known. The most
recent addition to the family of hardware stream ciphers is ZUC [44], designed
by the Data Assurance and Communication Security Research Center of the
Chinese Academy of Sciences. This cipher has been proposed for inclusion