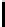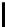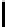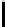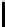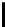Cryptography Reference
In-Depth Information
middle up to the right end. Two copies of an l-byte IV, denoted by an array
iv[0,...,l−1], are used as follows. The IV bytes are stored from index
2
−1
down to
2
−l in order from the least significant byte to the most significant
byte. The same IV bytes are repeated from index
2
up to
2
+ l − 1. The
former copy is used in the leftward movement of the index i and the latter
during the rightward movement. N is assumed to be even, which is the case
in standard RC4. For simplicity, an array IV of length N can be declared
with IV [y] = 0 for those indices which do not contain any IV byte.
8
<
:
iv[
2
for
2
−l ≤y ≤
2
−1−y]
−1;
iv[y−
2
]
for
2
≤y ≤
2
IV [y] =
+ l−1;
0 otherwise.
For N = 256 and l = 16, this scheme places 16 × 2 = 32 many bytes in
the middle of the IV array spanning from index 112 to 143. Use of IVs in the
above manner has two implications.
1. Repeating the IV bytes creates a dependency so that one cannot choose
all the 32 bytes freely to find some weakness in the system, since one
byte at the left corresponds to one byte at the right, when viewed sym-
metrically from the middle of an N-byte array.
2. Moreover, in two different directions, the key bytes are added with the IV
bytes in an opposite order. Apart from the 2l many operations involving
the IV , the rest of N−2l many operations are without the involvement
of IV in Layer 2. This helps in covering the IV values, and chosen IV
kind of attacks will be hard to mount.
Layer 2: Scrambling with IV
For i =
2
Layer 3: Zigzag Scrambling
For y = 0,...,N −1
If y ≡ 0 mod 2 then
i =
2
;
−1 down to 0
j = (j + S[i])⊕(K[i] + IV [i]);
Swap(S[i],S[j]);
Else
i = N −
y+
2
;
j = (j + S[i] + K[i]);
Swap(S[i],S[j]);
For i =
2
,...,N −1
j = (j + S[i])⊕(K[i] + IV [i]);
Swap(S[i],S[j]);
In the third and final layer, more scrambling is performed in a zigzag
fashion, where the deterministic index i takes values in the following order: 0,
255, 1, 254, 2, 253, ..., 125, 130, 126, 129, 127, 128. In general, for y varying
from 0 to N −1 in steps of 1, we can write
y
2
if y ≡ 0 mod 2;
i =
N −
y+1
2
if y ≡ 1 mod 2.
We write the steps of KSA
+
in Algorithm 9.4.1.
More scrambling steps definitely increases the cost of the cipher. The
running time of the KSA
+
is around three times that of RC4 KSA, since there