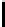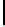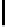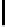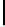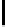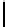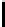Cryptography Reference
In-Depth Information
Further, though c
i
's are elements of Z
N
, the coe
cients set of the c
i
's are
restricted to {−1,0,1}. This gives 256 groups of 3
4
= 81 linear equations for
each round. Experimental verification of these equations with 10
9
randomly
chosen secret keys of 16 bytes reveals the already known biases as well as some
new biases. In Table 5.7, we present some of the new biases reported in [158].
c
0
c
1
c
2
c
3
C Probability
0
0.89
N
1
1
-1
1
.
.
.
.
.
.
1.25
N
0
1
1
-1
255
0.95
N
0
1
1
1
0
.
.
.
.
.
.
0.95
N
0
1
1
1
255
0.95
N
1
1
0
0
0
.
.
.
.
.
.
0.95
N
1
1
0
0
255
2
N
1
1
-1
0
i
2
N
1
-1
1
0
i
0.9
N
1
-1
0
0
1
.
.
.
.
.
.
1.25
N
1
-1
0
0
255
TABLE 5.7: Some keystream-state correlations as observed in [158].
To achieve faster than exhaustive search, the work [158] proposed a spectral
approach that revealed some more new biases. Additionally, some new biases
involving the secret key bytes were also found by considering the following
linear model.
a
0
K[0] ++ a
l−1
K[l−1] + a
l
z
1
++ a
2l−1
z
l
= b.
(5.3)
Some of the new secret key biases are presented in Table 5.8.
Relation Probability
z
1
+ K[0] + K[1]−K[2] = 3
1.14116
N
z
2
+ K[1] + K[2] = −3
1.36897
N
1.04463
N
z
4
−K[1] + K[4] = 4
TABLE 5.8: Some keystream-key correlations as observed in [158].
Proofs of these biases have recently been published in [156].