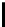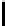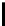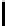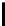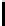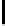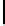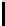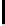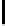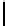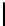Cryptography Reference
In-Depth Information
n
m
l n m
|EI
m
|
8l
e P(c
N,n
≥ m)
5
48
5
1712304
238500
40
25.6
0.431
5
24
5
42504
7500
40
20.3
0.385
5
16
5
4368
810
40
17.0
0.250
8
22
6
74613
29646
64
31.9
0.414
8
16
6
8008
3472
64
28.8
0.273
8
20
7
77520
13068
64
23.4
0.158
10
16
7
11440
5840
80
36.5
0.166
10
24
8
735471
130248
80
34.0
0.162
12
24
8
735471
274560
96
51.1
0.241
12
24
9
1307504
281600
96
43.1
0.116
12
21
10
352716
49920
96
31.6
0.026
16
24
9
1307504
721800
128
75.5
0.185
16
32
10
64512240
19731712 128
73.2
0.160
16
32
11
129024480
24321024 128
65.5
0.086
16
40
12
5586853480 367105284 128
61.5
0.050
16
27
12
17383860
2478464
128
53.2
0.022
16
26
12
9657700
1422080
128
52.4
0.019
16
44
14
114955808528 847648395 128
46.9
0.006
16
24
14
1961256
69120
128
32.2
0.0006
TABLE 4.1: Running the RecoverKey algorithm using different parameters
for the final permutation after the complete KSA (with N = 256 rounds).