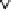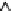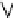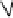Cryptography Reference
In-Depth Information
Transmission Error, E(t)
R'(t)=R(t)+E(t)
R(t)
Inverse
Quantization
Quantization
+
+
Input Video
Gain
α
Output Video
+
Gain
Leaky Factor
α
In-Loop
Frame Buffer
Leaky Factor
In-Loop
Frame Buffer
Decoder
Encoder
Fig. 3.15.
Configuration of prediction loop for leaky prediction.
GOP Boundary
L
3
H
1
H
1
H
1
H
1
L
3
H
2
H
3
H
2
SNR Enh. Layer 2
160kbits/s
L
3
H
1
H
1
H
1
H
1
L
3
H
2
H
3
H
2
Spatial Enh . Layer
(CIF)
SNR Enh. Layer 1
160kbits/s
CIF 30Hz: 160-480kbits/s
CIF 15Hz: 80-240kbits/s
CIF 7.5Hz: 40-120kbits/s
CIF 3.75Hz: 20-60kbits/s
L
3
H
1
H
1
H
1
H
1
L
3
H
2
H
3
H
2
SNR Base Layer
80kbits/s
Inter-Layer Predcition
A
B
2
B
2
B
1
SNR Enh. Layer 2
(Dead sub-stream)
40kbits/s
A
B
2
B
2
B
1
Spatial Base Layer
SNR Enh. Layer 1
40kbits/s
QCIF 15Hz: 40-120kbits/s
QCIF 7.5Hz: 20-60kbits/s
QCIF 3.75Hz: 10-30kbits/s
A
B
2
B
2
B
1
A
SNR Base Layer
40kbits/s
Temporal Enh . Layer 1
Temporal Enh . Layer 2
Temporal Enh . Layer 3
Temporal Base Layer
Fig. 3.16.
Example of combining spatial, temporal, and SNR scalability.