Cryptography Reference
In-Depth Information
different number of descriptions received, and obtain different qualities of the
reconstructed image.
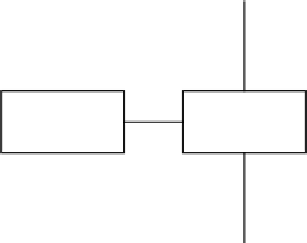
Channel 1
Decoder 1
β
1
X
(1)
i
1
X
Encoder
α
0
Decoder 0
β
0
X
(0)
Source
i
2
Decoder 2
β
2
X
(2)
Channel 2
Fig. 12.1.
The generic model for MD source coding with two channels and three
receivers. The general case has K channels and 2
K
−1 receivers.
In addition to making theoretic researches, it is also important to de-
vise practical designs to make MDC applicable with the situation depicted in
Fig. 12.1. Practical applications and implementations of MDC emerged in the
nineties. Two major categories for MDC applications are:
(i)
quantization based
schemes, such as Multiple Description Scalar Quan-
tization (MDSQ) [27] and Multiple Description Vector Quantization
(MDVQ) [28], and
(ii)
transform-domain based
schemes, called Multiple Description Transform
Coding (MDTC) [29, 30].
In this chapter, we focus on quantization based MD schemes for watermarking.
Operations and realizations of quantization-based MDC will be described in
Sec. 12.3. The idea for watermarking with MDTC is basically the same as that
with MDVQ. However, even though watermarking with MDTC has the same
design as MDVQ conceptually, the design and implementation of algorithm
needs to be done by other means. These will not be addressed here. We will
concentrate in watermarking with quantization-based MDC.
12.3 Quantization Based Multiple Description Coding
Applications of MDC focus on error concealment and error resilience. In
this chapter, we introduce an idea of how to apply MDC with watermark-
ing schemes to cover both the reconstructed image quality after reception,
and the ownership of the original image.