Cryptography Reference
In-Depth Information
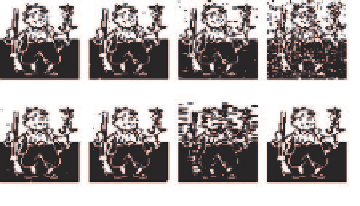
(a)
(b)
(c)
(d)
(e)
(f)
(g)
(h)
Fig. 11.19.
Invisible watermarks extracted from the attacked watermarked images.
(a) JPEG compression QF = 70%, NHS = 1.0000; (b) JPEG compression QF =
60%, NHS = 0.9976; (c) 33 median filtering, NHS = 0.9744; (d) 22median
filtering, NHS = 0.8723; (e) Gaussian filtering 33, NHS = 0.9954; (f) Contrast
enhancement by 30%, NHS = 0.9966; (g) A quarter of the image in the upper-left
corner cropped, NHS = 0.8549; (h) Visible watermark removing, NHS = 1.0000.
amount of audiovisual information available in digital format has grown ex-
ponentially in recent years. This has resulted in an information explosion
that has exceeded the limit of human capability. Digitization, compression,
and archival of multimedia information has become popular, inexpensive and
straightforward. Subsequent retrieval of the stored information may require
considerable additional work in order for it to be effective and e
cient. The
second problem is that there is almost no limit for anyone to make unlimited
copies of digital contents on the Internet and by means of CD-ROM. This is
a major disadvantage from the owners viewpoint when entering the digital
world. Copyright protection has therefore been one of the most important is-
sues in the digital world. This chapter is concerned with the problems in image
retrieval and copyright protection. The first question is whether we should use
some effective retrieval methods to get the desired images. In typical Content-
Based Image Retrieval (CBIR) systems [32], the visual contents of the images
in the database are extracted and are described by multi-dimensional fea-
ture vectors. The feature vectors form a feature database. To retrieve images,
users provide the retrieval system with example images or sketched figures.
The similarities and distances between the feature vectors of the query ex-
ample or sketch and those of the images in the database are then calculated.
Retrieval is accomplished with the aid of an indexing scheme. Recent retrieval
systems have incorporated users relevance feedback to modify and improve
the retrieval process. The existing image retrieval algorithms can be classified
into two classes. That is, Low-Level Based and High-Level (semantic) Based.
The low-level features include color [33], texture [34], shape [35] and spatial
relationships [36]. Some retrieval methods based on semantic-level [37] have
been recently proposed.
On the latter issue, encryption may provide one of solutions. However,
conventional cryptographic systems permit only valid keyholders access to