Cryptography Reference
In-Depth Information
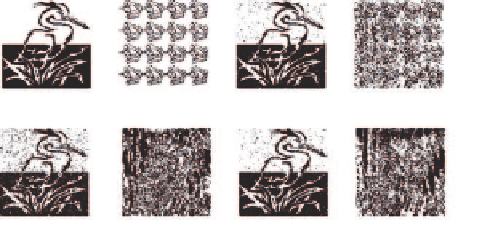
(a)
(b)
(c)
(d)
Fig. 11.11.
The VQ compressed watermarked images. (a) By Codebook 1. (b) By
Codebook 2. (c) By Codebook 3. (d) By Codebook 4.
(a)
(b)
(c)
(d)
(e)
(f)
(g)
(h)
Fig. 11.12.
The watermarks extracted from VQ compressed watermarked images.
(a) The robust one extracted from Fig. 11.11(a), NHS = 1.0. (b) The semi-fragile
one extracted from Fig. 11.11(a), NHS = 1.0. (c) The robust one extracted from
Fig. 11.11(b), NHS = 0.945. (d) The semi-fragile one extracted from Fig. 11.11(b),
NHS = 0.604. (e) The robust one extracted from Fig. 11.11(c), NHS = 0.851. (f)
The semi-fragile one extracted from Fig. 11.11(c), NHS = 0.069. (g) The robust one
extracted from Fig. 11.11(d), NHS = 0.943. (h) The semi-fragile one extracted from
Fig. 11.11(d), NHS = 0.189.