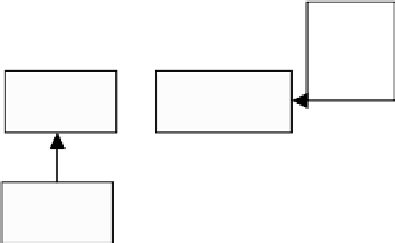Cryptography Reference
In-Depth Information
Input
Encoded
Indices
Nearest
Neighbor
VQ Encoder
Division
X
Vectors
+
_
Codebook
C
1
+
X
1
Ouput
X
′
Normal VQ
Composition
Vectors
Decoder
P
Index Polarities
Computation
Embedding
key
2
W
W
R
Permutation
key
1
Fig. 11.2.
The robust watermark embedding process of the first stage.
Because each index has n
2
bits, we can select an embedding position from n
2
candidate positions. Assume that we select Position key
3
, which is considered
as a key, to embed the watermark bit. Here 0≤key
3
−1. Unlike the
normal VQ encoder, the embedding process for each watermark bit can be
done by searching for the best match codeword c
2p
for each input error vector
x
1
. This has the constraints that the key
3
-th bit of index p is equal to the
watermark bit to be embedded. After applying the normal VQ decoder, we
can obtain the reconstructed error image X
′
1
≤n
2
as follows
′
1
−1
[ICVQ
2
[X
1
]] .
X
=VQ
2
(11.11)
We can then obtain the final watermarked image X
W
as follows
′
′
X
W
= X
+ X
1
.
(11.12)
The Extraction Process
To enhance the security of the embedding process, we use the equivalent prod-
uct codebook C in the extraction process as shown in Fig. 11.4. That is to say,
the two-stage codebooks are used as secret keys while the product codebook
is available to users. The users do not know the codebook sizes used in two-
stage VQ or, how to segment the overall index into two stage indices is also
a secret key, key
5
. In order to make the embedding algorithm more secure,
we can also permute the product codebook and then give the permuted code-
book C
u
for users. The extraction process can be done without the original