Cryptography Reference
In-Depth Information
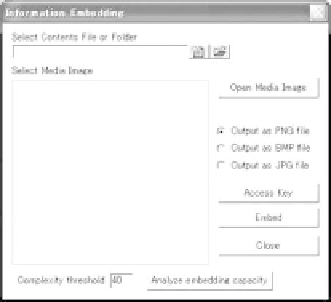
Fig. 8.17.
Information embedding component.
the embedding capacity is always the same, and it is analyzable before actual
embedding operation if a complexity threshold value is given. The threshold
value can be formally set at any value ranging from 0 to 55. However, accord-
ing to our experience, the best selection is to set it 40 or around. Therefore,
the default complexity threshold was set 40. However, in JPG case the embed-
ding capacity is not analyzable before embedding. If an access key is used in
embedding, then it must be also used in the extracting operation. The length
of the key was designed to have 4 to 16 bytes of alphanumeric characters. It
is not an ordinary password, but is a set of special embedding parameters in
the algorithm.
Information Extracting
The information extracting component of the system is illustrated in Fig.
8.18. This component extracts the embedded information data, i.e., files and
folders, out of a stego image of BMP, PNG, and JPG file.
The Access Key must be provided in the same way as was given in embed-
ding. Also, the complexity threshold value must be the same. The extraction
mode is either As it is or Link to Web. The As-it-is mode extracts the
embedded data just as it was when embedding. Link-to-Web mode operates
differently. In this mode, if the program finds an index.html file right un-
der the top-folder, then after extracting, the program will start running the
index.html file immediately. This operation can lead the system user (some-
one who runs the extracting program) to the WWW world instantly without
starting a Web browser manually. This operation can seamlessly connect the
users to a special information content space that is controlled by its owner,
or by someone who embedded the content.