Cryptography Reference
In-Depth Information
0.2
8th
6th
3rd
1st
0.15
0.1
0.05
0
0.05
0.1
0.15
0.2
0.25
0.3
0.35
0.4
delta
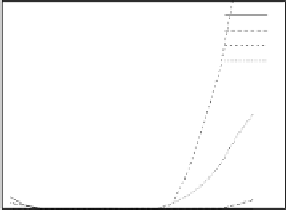
Fig. 8.8.
Error of histogram adjustment.
8.3.3 Experiments and Discussions
We investigated the relation between δ and the accuracy of the adjusted com-
plexity histogram. In the experiments, all of noise-like blocks in the cover
image are replaced with random binary sequences representing secret data.
In order to evaluate the accuracy in adjusting the shape of the complexity
histogram, we defined the measure of the accuracy as follows,
error =
h
o
(i)−h
e
(i),
(8.17)
i
where h
o
(i)andh
e
(i) represent the histograms of the cover image and the
stego image, respectively.
The error was calculated from δ =0.04 to 0.36 with 0.02 increments.
The result is shown in Fig. 8.8. As can be seen, the shape of the complexity
histogram with 0.1≤δ≤0.25 is virtually identical before embedding and
after embedding.
8.3.4 Conclusions
We have proposed an improved BPCS steganography technique that removes
an identifying signature that can be found in conventional BPCS steganog-
raphy. The improved BPCS is robust against attacks using complexity his-
togram because the complexity distribution is quasi-preserved by adjusting
the complexity of the embedded patterns.
8.4 Visual Attack to BPCS Steganography
and Countermeasure
BPCS replaces noisy blocks on bit-planes with the binary patterns mapped
from secret data. The complexity is used to determine whether blocks are