Cryptography Reference
In-Depth Information
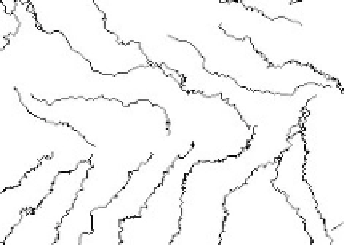
(a) Original map of river
(b) Watermarked map
Fig. 6.13.
Original map and watermarked map.
by use of this scheme. After the hidden data has been successfully extracted,
the cover map is recovered. Experimental results indicate that the recovered
map is exactly the same as the original map as their MD5 hashes matched
exactly.
6.3.3 Summary
This section discusses the issue of Reversible Data Hiding in vector maps. Two
algorithms are introduced. The first is implemented in the integer DCT do-
main. The high correlation of the map coordinates and the energy compaction
property of DCT are utilized by the scheme. The hidden data is embedded
by modifying the amplitude of the integer DCT coe
cients. The distortions
in this scheme are not easy to control. The second scheme is implemented in
the spatial domain and are based on Difference Expansion. A relatively high
capacity can be achieved and the induced distortions can be well controlled.
Some defects are apparent in the analyzing powers of the algorithm.
Firstly, the invisibility of the scheme could not be good. Since the hidden
data is embedded into the x (or y) coordinates, the movement directions of
the vertices are restricted to the x or y directions. Consequently, the shape of
the watermarked map has disturbed appearance. This degrades the invisibility
of the scheme. Secondly, the payload of the scheme depends to some extent
on the type of map. The type of the cover map determines the correlation
of its raw coordinates. Some maps do not have highly correlated coordinates.
For example the contour maps with large scales. The low correlation of the
coordinates could result in a reduced capacity.
6.4 Fragile Watermarking
As described in Section 6.1.1, there are some special applications where a
higher security level is required. As an instance, secret military maps must be