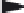Cryptography Reference
In-Depth Information
|DCT Coefficient|
|DCT Coefficient|
|
A
7
|=|
A
7
|+
A
MAX
A
MAX
|
A
7
|
A
1
A
2
A
3
A
4
A
5
A
6
A
7
D
A
1
A
2
A
3
A
4
A
5
A
6
A
7
D
embed bit '0'
embed bit '1'
Fig. 6.11.
The embedding method of [23].
of the highest frequency coe
cient,A
7
, is the smallest in most cases. It is
generally smaller than the maximum absolute value from A
1
to A
6
(denoted
as A
max
= maxA
1
). If the embedded bit 0, the unit remains
unchanged. If the embedded bit 1, the coe
cient A
7
is modified toA
′
,,A
6
=
7
A
7
+ A
max
. The above embedding method is reversible because the original
A
7
could be obtained by subtracting A
max
from A
′
7
after the extraction of
the hidden bit. This scheme is the first algorithm where the idea of reversible
data hiding is introduced into watermarking digital vector maps. A drawback
of the scheme is that the distortions induced by watermarking is relatively
too large. The authors have made some compensation.
6.3.2 Difference Expansion Scheme
Basic Idea of Difference Expansion
Difference expansion is a method of reversibly hiding data in pixel images, and
was first proposed by Tian [21]. The basic idea of difference expansion is to
utilize the high correlation of the cover data. For a pair of adjacent elements
denoted as integers x
1
and x
2
, which are highly correlated cover data, an
integer transform is defined to calculate their difference (d) and integer-mean
(m). It is shown in Eqn. (6.5):
−x
2
,
m =floor
d = x
1
(6.5)
x
1
+x
2
2
.
The transform is strictly invertible and the Eqn. (6.6) is the inverse transform:
d+1
2
x
1
= m +floor
,
(6.6)
d
2
x
2
= m−floor
.
To hide data bits, x
1
and x
2
are transformed to d and m by Eqn. (6.5).
The high correlation of the cover data means that two elements x
1
and x
2