Cryptography Reference
In-Depth Information
DWT Domain Schemes
Li and Xu proposed a blind scheme [13], which consists of embedding multiple
bits into a vector map in DWT domain. The main idea of the scheme is
described as follows.
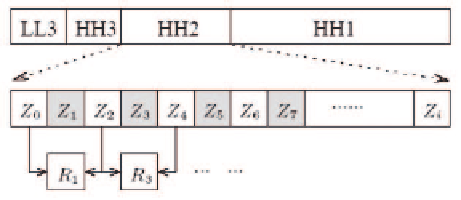
(I) Similar to works [9, 10], the coordinates of the vertices are first com-
bined to a complex sequence. Then a three level wavelet decomposition
is performed on the sequence, which results in four sub-bands, i.e. HH1,
HH2, HH3, LL3. Considering maps precision tolerance, HH2 and HH3
are selected for embedding data.
(II) Taking the coe
cients in HH2 as an example, the embedding method
is shown in Fig. 6.5.
Fig. 6.5.
An illustration of the DWT scheme in [13].
The values Z0,Z1,,Zi are the coe
cients in HH2. Starting with
Z1, the watermark bits will be embedded into every other coe
cient.
That is, the coe
cients with odd index (shadowed) Z1,Z3,Z5,.
For example, suppose embedding the first watermark bit w
1
∈0, 1
into Z1. A reference value R is calculated by R
1
=
Z
0
+Z
2
α.Two
neighboring coe
cients Z
0
and Z
2
areusedandα is the power factor
controlling the embedding amplitude. Calculate K
1
= round(Z
1
2
/R
1
)
and use the parity of K
1
as the representation of a watermark bit.
If w
1
=0,modifyZ
1
to make K
1
be an even number. If w
1
=1,
to make K
1
be an odd number. The other watermark bits
w
2
,w
3
,are embedded into Z
3
,Z
5
,in the same way.
(III) The data extraction can be performed without using the original map.
Wavelet decomposition and K
modifyZ
1
′
i
(i =1, 3,) are calculated and water-
mark bits can be extracted according to the parity of each K
′
i
.
In this scheme, the amplitude of the coordinates DWT coe
cients are
modified to specific modes for representing the watermark bits. The scheme
is robust to noise and some geometrical attacks. Like other algorithms in
transform domains, it is fragile to vertex attacks such as map simplification
or interpolation.