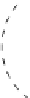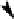Cryptography Reference
In-Depth Information
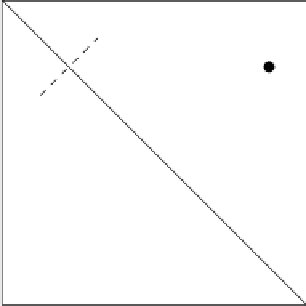
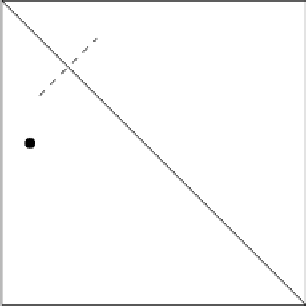
Mask of Pattern 1
upper triangle
Mask of Pattern 0
upper triangle
lower triangle
lower triangle
(a) Vertex pattern of bit 1
(b) Vertex pattern of bit 0
Fig. 6.1.
Two patterns representing 1 and 0 (algorithm in [3]).
Schulz and Voigt [4] proposed a high capacity scheme which is robust to
noise and simplification attacks. In the scheme, the original map is divided
into many vertical and horizontal strips. The width of the strips could be
4
3
τ
√
2
to ensure the max distortion below the tolerance τ . The vertices within
a strip are shifted to the reference line which is used to represent bit 1 or 0.
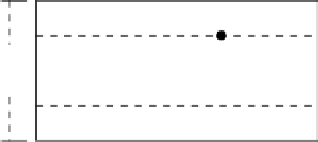
Figure 6.2 demonstrates the shifting process. The extraction of the hidden bit
will depend on the half of the strip where most vertices located. The algorithm
could survive additive noises with the amplitude less than 1/4ofthestripe
width.
1
1
0
0
(a) Embed 1 in a strip
(b) Embed 0 in a strip
Fig. 6.2.
Embedding data in a strip.
The algorithm proposed by Huber [5] also uses the locational relationship
between vertices to hide bits. The scheme is different from those mentioned
previously, in which new vertices are interpolated for data embedding. Fig-
ure 6.3 is an example of this scheme.