Cryptography Reference
In-Depth Information
Fig. 5.8.
An example of the cluster ordering-and-mapping technique.
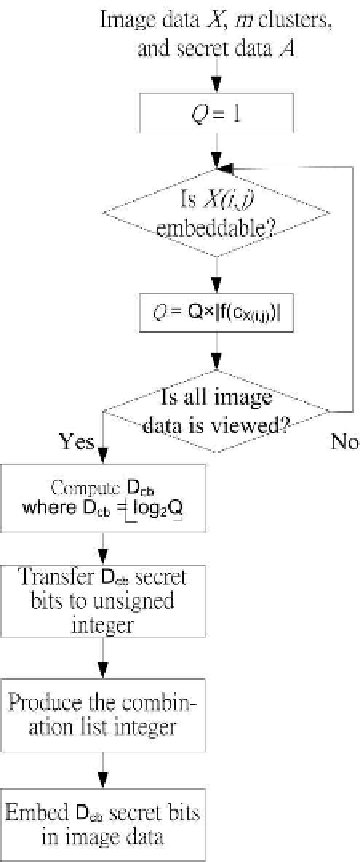
To determine the size of the secret bits that can be embedded in cover
image, we need to calculate the product value Q,
h
w
Q =
f (c
X(i,j)
)
.
(5.8)
i=1
j=1
We
can
then
calculate
the
hiding
capacity
D
cb
of
the
combination
technique,