Cryptography Reference
In-Depth Information
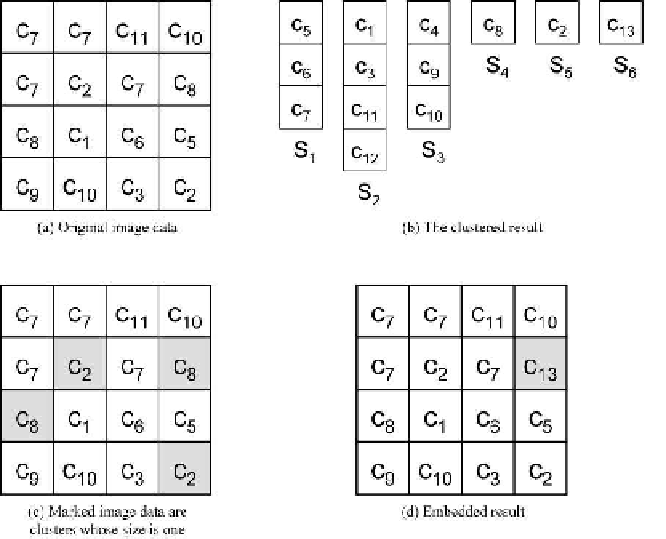
In this example, the image data X(2, 2), X(2, 4), X(2, 4), and X(4, 4)
shown in Fig. 5.7(c) are embeddable and they satisfy
=1.We
then try embedding four bits into those image data. Since the cluster ordering-
and-mapping functions of X(2, 2), X(3, 1), and X(4, 4) are equal to the secret
bits, this image data is that of the secret bits which already exist. While the
cluster ordering-and-mapping function of X(2, 4) is not equal to the secret
bit, we modify this color using the closest color that satisfies the replacement
conditions. Therefore, color c
13
is used to replace color c
8
, and this result is
shown in Fig. 5.7(d).
f (c
X(i,j)
)
Fig. 5.7.
An example of the cluster ordering-and-mapping technique.
On the second round, the combination technique is employed to embed the
secret data into the image data. The flowchart of the combination technique
is shown in Fig. 5.8. The combination technique was first proposed by Du
et al. [15] to embed the secret data into the compressed codes of VQ. The
combination technique uses the ordered list formed by element combination of
the clusters which each color of the cover image I. The secret data represented
by a bit stream can be transformed to a corresponding unsigned integer. The
unsigned integer is represented by the order of element combination.