Cryptography Reference
In-Depth Information
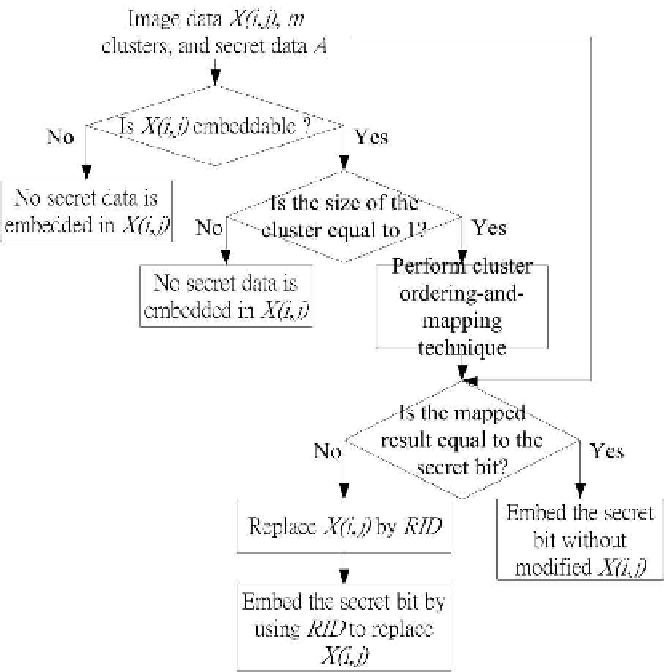
Fig. 5.6.
Flowchart of the cluster ordering-and-mapping technique.
3. The color c
RID
is an embeddable pixel.
The image data X(i, j) of the nearest color is used for the modification.
Let D
om
denote the hiding capacity of the cluster ordering-and-mapping
technique. The formula for calculating D
om
is,
h
w
D
om
=
f (c
X(i,j)
)
,
if
f (c
X(i,j)
)
=1.
(5.7)
i=1
j=1
Here
is the size of the cluster to which the color c
X(i,j)
belongs.
An example of the cluster ordering-and-mapping technique is shown in
Fig. 5.7. Assume the cover image I with the image dataX
1,1
,X
1,2
,,X
4,4
f (c
X(i,j)
)
is as shown in Fig. 5.7(a). We have six clusters that are shown in Fig. 5.7(b).
Let A = (1011011)
2
be the secret data.