Cryptography Reference
In-Depth Information
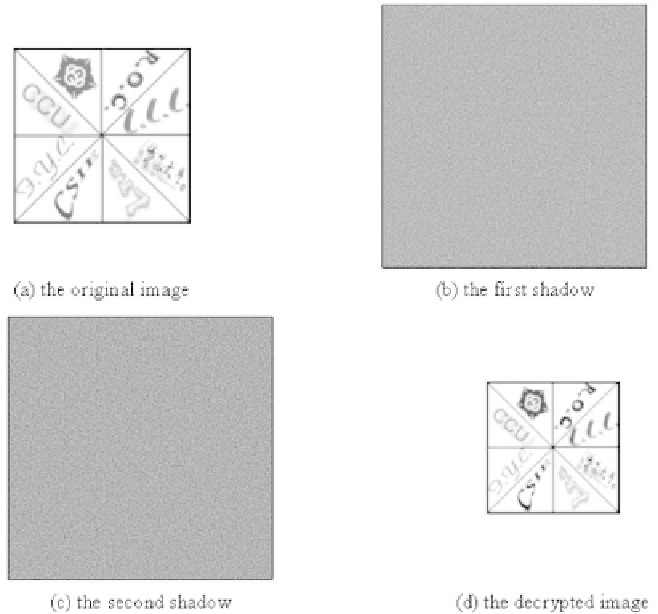
In the first experiment, the proposed (2, 2)-VSS scheme is implemented
and tested on an input image of size 512512, which is shown in Fig. 4.13(a).
The image consists of eight secret images. The codebooks C
0
and C
1
used in
the experiment are
⎨
0, 0, 1, 1
1, 1, 0, 0
0, 1, 0, 1
1, 0, 1, 0
0, 1, 1, 0
1, 0, 0, 1
,
,
C
0
=
and
⎩
1, 0, 0, 1
0, 1, 1, 0
1, 0, 1, 0
0, 1, 0, 1
1, 1, 0, 0
0, 0, 1, 1
,
,
⎧
⎨
0, 0, 1, 1
0, 0, 1, 1
0, 1, 0, 1
0, 1, 0, 1
0, 1, 1, 0
0, 1, 1, 0
,
,
C
1
=
.
1, 0, 0, 1
1, 0, 0, 1
1, 0, 1, 0
1, 0, 1, 0
1, 1, 0, 0
1, 1, 0, 0
⎩
,
,
After the encryption process, the scheme generates the two shadows shown
in Fig. 4.13(b) and Fig. 4.13(c). Following the decryption process, the recon-
structed image is obtained and is shown in Fig. 4.13(d).
Fig. 4.13.
The (2, 2)-VSS scheme on the input image of size 512512.