Cryptography Reference
In-Depth Information
a
j,χ
2
k
, by using the decryption function f
d CLF TN
to reconstruct the original
sub-region T
i
. The function f
d CLF TN
is defined as follows
f
d CLF TN
(a
j,1
i
,a
j,2
i
,,a
j,n
i
)=
if a
j,1
iγ
∩a
j,2
iγ
∩∩a
j,n
iγ
′
1
′
1
′
1,
∈C
∈C
∈C
1
;
(4.8)
0,
otherwise,
where a
j,χ
iγ
is the γ-th block of a
j,χ
i
.LetT
iγ
= f
d CLF TN
(a
j,1
i
, a
j,2
i
,, a
j,n
i
)
where T
iγ
is the γ-th bit of T
i
.
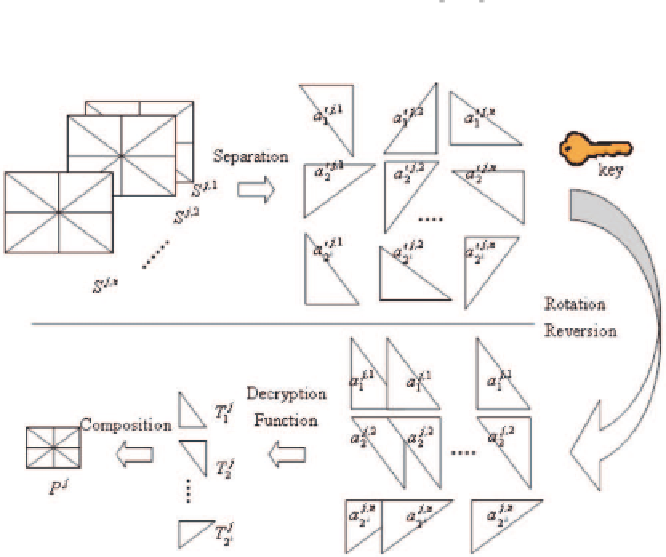
Fig. 4.12.
Diagram of (t, n)-VSS bit plane reconstruction process for the binary
plane P
j
.
The scheme finally reconstructs the binary plane P
j
and stacks the planes
obtained to reconstruct the gray-scale image. The secret images can then be
displayed by the human visual system.
4.5 Experiments and Results
In this section, the results obtained using our encrypted and decrypted
schemes for information secret sharing are presented respectively and dis-
cussed in different applications to illustrate the e
ciency and effectiveness.