Cryptography Reference
In-Depth Information
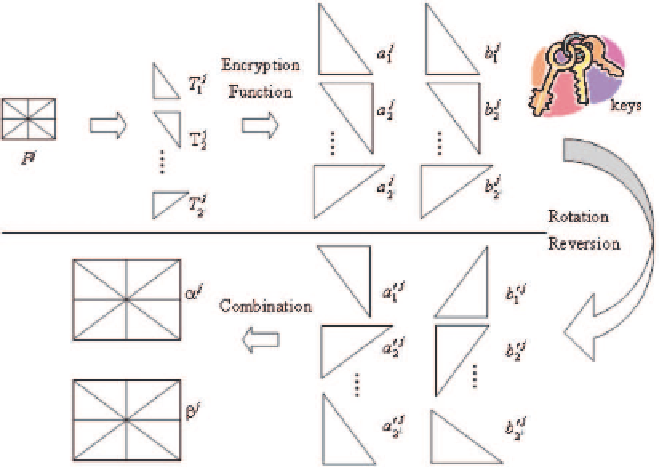
Fig. 4.6.
Diagram of (2, 2)-VSS shadow generation process for the binary plane P
j
.
black, then the blocks are selected from C
1
. After finishing the encryption, we
have two sub-shadows, a
i
and b
i
, for the sub-region T
i
.
Some bits will be out of range of the shadow when the bits are expended
into the block by using Naor and Shamirs encryption function. For example,
Fig. 4.7(a) shows a sub-region with a triangle shape. Fig. 4.7(b) is one of the
generated shadows in the sub-region. In Fig. 4.7(b), some bits are scattered
outside the diagonal of the shadow. The scheme ignores the bits not in the
range of the shadow. In order to ensure the correction of the decryption bit,
the scheme assigns the specific blocks for the bits on the diagonal of the sub-
region. For example, in Fig. 4.7(a), the bits on the diagonal are 0, 0, 0, 1, and
00
11
00
11
0. For the bit with value 0, the scheme assigns the blocks
and
for the first sub-shadow a
i
and the second sub-shadow b
i
, respectively. For the
bit with value 1, the scheme assigns the blocks
10
10
01
01
for a
i
and
and
b
i
, respectively.
In order to increase the complexity and enhance the security of the
proposed scheme, the sub-shadows are placed in different locations of the
plane by using a secret key. The scheme generates two random sequences,
RA
j
rb
2
k
) for the j-th plane P
j
by using the secret key, which is only known to the participants. Then, the
scheme moves the i-th sub-shadow a
i
ra
2
k
)andRB
j
=(ra
1
ra
2
=(rb
1
rb
2
to the ra
i
-th location of the newly con-