Cryptography Reference
In-Depth Information
“receipt,” which one may believe or not, is, of course, inadequate. A certificate
is rather a data set that has been formatted according to some standard
13
that
among other things speaks to the identity of
A
as well as her public key and that
itself has been digitally signed by the certification authority.
The genuineness of a participant's key can be verified with the help of
the information contained in the certificate. Applications that support such
verification in software already exist. The future multiplicity of such applications,
whose technical and organizational basis will be based on so-called
public key
infrastructures
(PKI), can today only be guessed at. Concrete uses are emerging
in the digital signing of e-mail, the validation of commercial transactions,
e-commerce and m-commerce, electronic banking, document management, and
administrative procedures (see Figure 17-1).
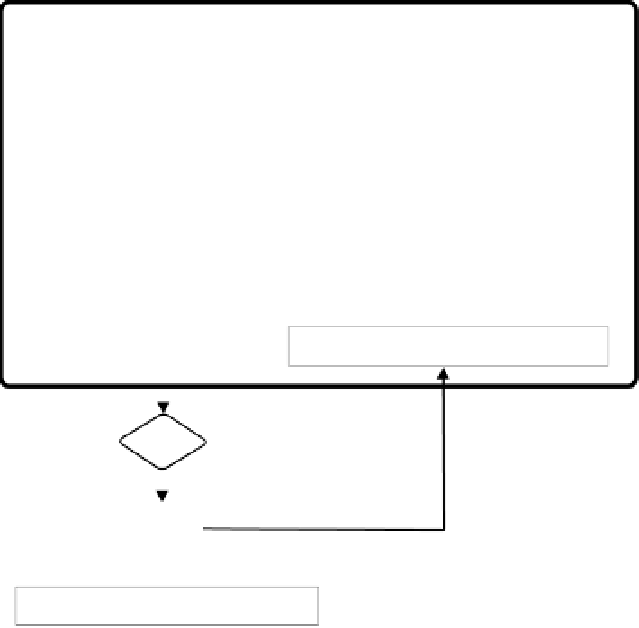
(Identifies the Version of the Certificate, e.g., V3)
(Unique Integer Identifier for the Certificate)
(Algorithm ID Used to Sign the Certificate)
(X.500 Distinguished Name of the Issuer)
(Not Before and Not After Validity Times)
(X.500 Distinguished Name of the Owner)
(Public Key of the Owner)
(Opt. Unique ID of the Issuing CA)
(Opt. Unique ID of the Owner)
(Optional Extensions)
Version
Serial Number
Signature
Issuer Name
Validity
Subject Name
Subject Public Key Info
Issuer Unique Identifier
Subject Unique Identifier
Extensions
Digital Signature of the
Certification Authority
1101 111100001 1101001001 1110...
Hashing
RSA
1001 11000101 111010101 1101 10...
Secret Key of the Certification Authority
Figure 17-1. Example of the construction of a certificate
On the assumption that
B
knows the public key of the certification authority,
B
can now verify the certificate presented by
A
and thereafter
A
's signature to
become convinced of the authenticity of the information.
13
Widely used is ISO 9594-8, which is equivalent to the ITU-T (formerly CCITT) recommenda-
tion X.509v3.