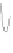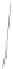Cryptography Reference
In-Depth Information
uous derivation, or increasing the size of the constellation to lower the central
lobe of the spectrum, mean an increase in the complexity of the modulator.
2.1.2 Linear Memoryless Modulations
Amplitude-shift keying with
M
states: M-ASK
Let us first note a particular case of amplitude modulation: On Off Keying
(OOK), for which
a
in the expression (2.1) takes the value
0
or
A
.Oneofthe
binary states therefore corresponds to an extinction of the carrier. The presence
or absence of the carrier can be recognized independently of the knowledge of the
phase
ϕ
, by measuring the energy of the received signal during a short interval
of time on the scale of period
1
/f
0
of the carrier wave, which is called
incoherent
detection
. Figure 2.1 shows the time interval of a signal modulated by On Off
Keying.
Figure 2.1 - On Off Keying (OOK).
In the general case of amplitude-shift keying (ASK) with
M
states, the am-
plitude of the carrier is the modulated value
a
j
=
A
j
h
(
t
)
for
j
=1
,
2
, ..., M
where
A
j
takes a value among
M
=2
m
values according to the group of data
presented at the input of the modulator and
h
(
t
)
is a rectangular pulse with
unit amplitude and width
T
. The modulator thus provides signals of the form:
s
j
(
t
)=
A
j
h
(
t
)cos(2
πf
0
t
+
ϕ
0
)
(2.5)
with
A
j
=(2
j
−
1
−
M
)
Aj
=1
,
2
,
···
,M
where
A
is constant
(2.6)
and
h
(
t
)=1
for
t
∈
[0
,T
[
(2.7)
=0
elsewhere
Amplitude
A
j
of the modulated signal is constant for a width
T
then changes
value; the modulated signal thus transmits
log
2
(
M
)
binary data every
T
seconds.
We can note that half the nominal amplitudes
A
j
are negative. The identity
a
cos
ϕ
=
a
cos(
ϕ
+
π
)
thus implies
coherent
demodulation where the phase
ϕ
is known. The phase often only being known to a multiple of
π
, a binary
message where the symbols are
−
±
1
will only be demodulated to one sign.