Cryptography Reference
In-Depth Information
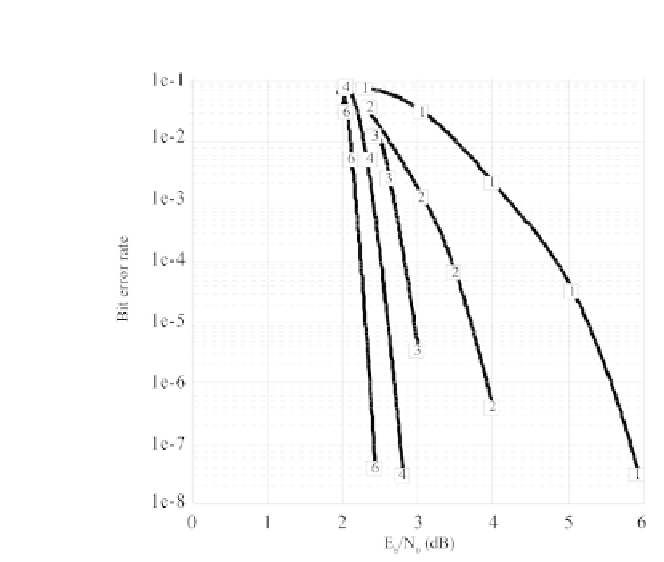
Figure 8.5 - Evolution of the binary error rate during Chase-Pyndiah turbo decoding
for 1, 2, 3, 4 and 6 iterations (BCH code(64,51,6), 2-PSK on a Gaussian channel).
•
Step 4: List the concurrent words in the order of increasing metrics
M
1
(we use a combination generation algorithm with exclusion). Stop as soon
as the total metric
M
begins to increase.
•
Step 5: After the inverse permutation of the metrics, calculate the extrinsic
values from the concurrent words by using the same equations as in the
Chase-Pyndiah algorithm.
Example 8.5
We consider the same example as for the Chase algorithm.
Let
r
=(0
.
5; 0
.
7;
0
.
3; 0
.
1; 0
.
6)
be a received sample. The parity
control matrix of the Hamming code of dimension 4 and length 7 is, as we have
already seen,
−
0
.
9; 0
.
2;
−
⎡
⎤
1110100
1101010
1011001
⎣
⎦
H
=
We have
r
•
=(
−
0
.
9; 0
.
7; 0
.
6; 0
.
5;
−
0
.
3; 0
.
2; 0
.
1)
and
P
=
Step 1:
[3
,
2
,
7
,
1
,
5
,
4
,
6]
.