Cryptography Reference
In-Depth Information
In a
Digital Signal Processor
(DSP) or in an
Application Specific Integrated
Circuit
(ASIC), it may be useful to have only to deal with positive numbers.
Law (1.11) can then be implemented as:
3
c
=
c
∈{
c
}
such that
(
V
max
+
x
j
X
j
)+(
V
max
+
y
j
Y
j
)
is maximum
(1.12)
j
=0
where
[
V
max
,V
max
]
is the interval of the values that the input samples
X
j
and
Y
j
of the decoder can take after the clipping operation.
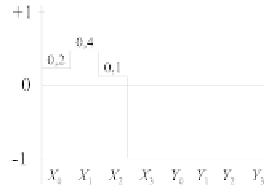
In Figure 1.4, the "all zero" codeword has been transmitted and received
with three alterations in the first three positions. These three alterations have
inverted the signs of the symbols but their amplitudes are at a fairly low level:
0
.
2
,
0
.
4
and
0
.
1
. Hard input decoding produces an erroneous result as the closest
codeword in terms of the Hamming distance is
(1
,
1
,
1
,
0
,
0
,
0
,
0
,
1)
. However,
soft input decoding according to (1.11) does produce the "all zero" word, whose
maximum scalar product is:
−
(
−
1)(0
.
2) + (
−
1)(0
.
4) + (
−
1)(0
.
1) + (
−
1)(
−
1)
+(
−
1)(
−
1) + (
−
1)(
−
1) + (
−
1)(
−
1) + (
−
1)(
−
1)
=
4
.
3
in comparison with:
(+1)(0
.
2) + (+1)(0
.
4) + (+1)(0
.
1) + (
−
1)(
−
1)
+(
−
1)(
−
1) + (
−
1)(
−
1) + (
−
1)(
−
1) + (+1)(
−
1)
=
3
.
7
for the competitor word
(1
,
1
,
1
,
0
,
0
,
0
,
0
,
1)
.
This simple example shows the interest of not excluding the reliability infor-
mation in decision taking, whenever possible.
Figure 1.4 - The "all zero" word (emission of symbols with the value -1) has been
altered during the transmission on the first three positions. The hard input decoding
is erroneous, but not the soft input decoding.
The ML decoding rules that we have just used in a specific example are easily
generalizable. However, we do realize that beyond a certain length of message,
such a decoding principle is unrealistic. Applying ML decoding to codewords