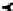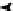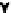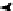Information Technology Reference
In-Depth Information
4 ABM and Arguments: NetArg
We used NetLogo [29] to develop NetArg
2
[14,16]: a model for simulating discus-
sions between argumentative agents, along with a software module (a NetLogo
add-on) that performes the computational argumentation analysis.
The model comprises a number of agents (100 in our experiments) distributed
in 20 distinct caves. Every agent reasons from the same set of arguments, and
she selects, with a fixed probability, one set of attack relations among the two
ones available at the beginning, as shown the
AF
s in Figure 2, derived from a
real debate in an online discussion forum about renewable energies
3
.Wetested
the model with different
AFs
, with random attacks and up to 10 arguments, as
well as
AFs
taken from empirical contexts and we found results to be stable.
At each time step, each agent is asked to start a dialogue with one of her
neighbors extracted at random (see Algorithm 1), who could be restricted to the
same cave or not, depending on the presence of bridges. The random extraction
assures that the probability to “argue” with members of the same cave is higher
than with out-cave neighbors, according to the fact that bridges (weak ties) are
less activated than strong ties.
a
c
a
c
b
b
e
e
d
d
(a) AF1
(b) AF2
Fig. 2.
The two argumentative frameworks distributed among the agents
The agent selected to start a dialogue picks one random argument in her
extensions (i.e., an argument she believes in) and addresses the previously se-
lected neighbor. The opponent replies, by following the dialogue procedure briefly
sketched in the previous section.
In all our experiments, we opted for the complete semantics, which agents
refer to when computing their extensions. At the beginning, each agent believes
either
or (
b,d
), the two possible extensions that a complete semantic
returns from the
AFs
used. It is evident from the two plots in Figure 3 that,
after some steps, agents adopt new opinions by means of dialogues: in (
a
)only
two bars are present at time 0, each of which represents one of the two extensions
available at the beginning (the distribution probability is set to 0.5 so they are
equally distributed); in (
b
) more bars are present at time 50, i.e. more extensions
are now available, because agents, by exchanging and accepting attacks, alter
their own arguments network and thus new extensions are possible.
{
a, c, e
}
2
The model can be downloaded from here: