Java Reference
In-Depth Information
Encrypting passwords
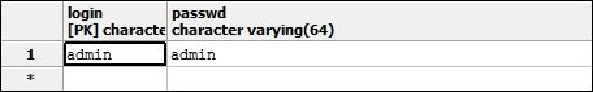
Storing passwords in the database as a clear text string is not considered a good practice;
as a matter of fact, a database has even more potential security holes than a regular
filesystem. Imagine, for example, that a DBA added a public synonym for some tables,
forgetting that one of those tables held sensitive information such as application pass-
words, as shown in the following screenshot! You then need to be sure that no potential at-
tackers will ever be able to deliver the following query.
Fortunately, securing application passwords is relatively easy; you can add a few extra op-
tions to your login module, specifying that the stored passwords are encrypted using a
message digest algorithm. For example, in the
Database
login module, you should add
the following highlighted options at the bottom:
<login-module code="Database" flag="required">
<module-option name="dsJndiName" value="java:jboss/
datasources/wflydevelopment"/>
<module-option name="principalsQuery" value="select
passwd from USERS where login=?"/>
<module-option name="rolesQuery" value="select role,
'Roles' from USER_ROLES where login=?"/>
<module-option name="hashAlgorithm" value="SHA-256"/>
<module-option name="hashEncoding" value="BASE64"/>
</login-module>
Here, we specified that the password will be hashed against an SHA hash algorithm; al-
ternatively, you can use any other algorithm allowed by your JCA provider.
Note
For an excellent introduction to hashing algorithms, refer to
http://www.unixwiz.net/tech-