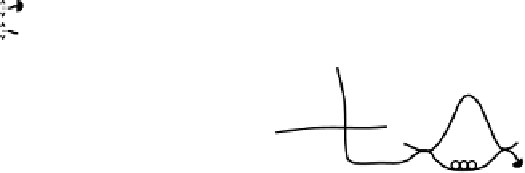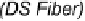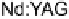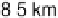Cryptography Reference
In-Depth Information
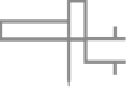
Figure 2.10
Schematics of the energy-time entanglement-based quantum QKD
system.
material to Bob and Charlie in a way that neither Bob nor Charlie alone
have any information about Alice's key. However, when comparing their
data, they have full information. The goal of this protocol is to force them to
collaborate.
In contrast to implementations using three-particle GHZ states [64,65],
pairs of time-bin entangled qubits were used to mimic the necessary quan-
tum correlation of three entangled qubits, albeit only two photons exist at the
same time (see Figure 2.11). This is possible thanks to the symmetry between
the preparation interferometer acting on the pump pulse and the interferom-
eters analyzing the down-converted photons. Indeed, the data describing the
emission of a bright pump pulse at Alice's is equivalent to the data charac-
terizing the detection of a photon at Bob's and Charlie's: all specify a phase
value and an output or input port, respectively. Therefore, the emission of a
pump pulse can be considered as a detection of a photon with 100% efficiency,
and the scheme features a much higher coincidence count rate compared to
the initially proposed GHZ-state type schemes.
2.5 The Future of Quantum Cryptography
What is the future of quantum cryptography? It is likely that it is still in its
infancy. Conceptually, as alluded to above, it is deeply rooted in the basic
aspect of quantum physics, i.e., in entanglement. On the applied side, it is
already attracting attention (and money) from industries and investors [30].
On the experimental side, quite a lot of progress is still to be expected, mainly
on two major specifications: the secret bit rate and the distance. These are not
independent but may be addressed in different, complementary, ways. First,
there is a mere technological approach: improve the detectors and/or the