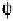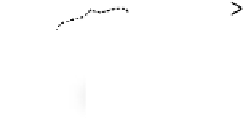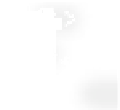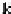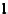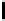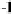Cryptography Reference
In-Depth Information
8.1 Introduction
Cryptography, i.e., the process of scrambling and encoding a plaintext into
a cyphertext and then back again, has been in use for centuries. Over time,
these techniques have evolved from simple substitution cyphers (where, for
example, a letter is replaced with another symbol) to a range of sophisticated
mathematical methods due to the advent of computers. Traditionally, cryptog-
raphy involves only two parties: the
sender
and the
receiver
, commonly know in
the literature as
Alice
and
Bob
. In some applications, however, the sender may
want to send the secret to more than one receiver so that only through collab-
oration can a subset of receivers recover it. This situation arises, for example,
when the sender cannot trust each receiver individually but can trust a num-
ber of receivers collectively. Protocols that facilitate this type of cryptocommu-
nication are known as
secret sharing
protocols. The role of Alice, or the sender,
is now replaced by a
dealer
who distributes the secret. The sole receiver, Bob, is
now replaced by a number of
players,
none of whom can be completely trusted.
An important class of secret sharing protocols is (
k, n
) threshold secret
sharing [1], in which the dealer encodes and distributes the secret information
to
n
players. Any subset of
k
players (
the access structure
) must collaborate to
retrieve the secret information, while the remaining recipients outside the
subset (
the adversary structure
) learn nothing, even when conspiring together.
This protocol is widely used to distribute information over classical networks
such as the Internet and distributed computer networks.
Quantum state sharing
is the quantum equivalent of classical secret sharing,
where the classical information is replaced by an unknown quantum state, as
illustrated in Figure 8.1. In the ideal case, the access structure can reconstruct
the secret quantum state perfectly, even though it appears partially destroyed
as a result of malicious and conspiring parties, or catastrophic quantum chan-
nel failures.
This chapter is structured in the following way: Section 8.2 gives the
reader some background information about classical secret sharing schemes.
Section 8.3 discusses how these concepts can be extended to distribute fragile
quantum states. It also shows the differences between quantum state sharing
ψ
in
access
structure
φ
n
dealer
φ
3
φ
n
-1
adversary
structure
φ
k
φ
2
φ
1
φ
k
-
1
φ
1
ψ
out
ψ
in
players
Figure 8.1
Illustration of a quantum state sharing protocol.