Cryptography Reference
In-Depth Information
6000
5900
5800
5700
g
=
30
5600
g
=
60
5500
5400
5300
9.6
×
10
-7
9.8
×
10
-7
1
×
10
-6
1.02
×
10
-6
1.04
×
10
-6
bit cell period
(
seconds
)
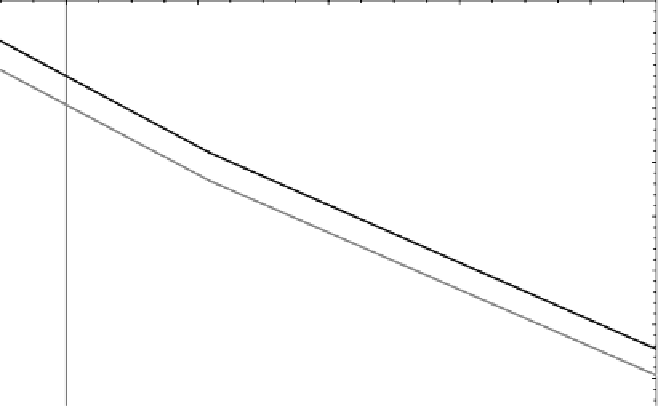
Figure 7.3
Effective throughput of secret Vernam cipher for different
g
values.
the method described in Ref. [7]. We assume the use of an attenuated, pulsed
laser, with Alice located on a low Earth orbit satellite at an altitude of 300
kilometers and Bob located at mean sea level, with the various system pa-
rameters corresponding to those for Scenario (
i
) in Section 5.3.2 in Ref. [7],
except that here the source of the quantum bits operates at a pulse repetition
frequency (PRF) of 1 MHz, and we specifically assume that the enemy does
not have the capability of making use of prior shared entanglement in con-
ducting eavesdropping attacks. We see that the additional cost incurred in
subtracting the amount required to achieve the required mutual information
bound and failure probability reduces the throughput rate by an amount that
is likely to be acceptable for most purposes. For instance, for a source PRF
of 1 MHz, we find that the throughput rate with a value of
g
PPA
=
30 is 5614
=
bits per second. With a subtraction amount of
g
PPA
60, the throughput rate
drops to 5563 bits per second [16].
7.4 Conclusions
We have presented results for the secrecy capacity of a practical quantum
key distribution scheme using attenuated laser pulses to carry the quantum
information and encoding the raw key material using photon polarizations
according to the BB84 protocol. This analysis of the secrecy of a practical
implementation of the BB84 protocol simultaneously takes into account and