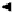Cryptography Reference
In-Depth Information
between high-intensity bursts, which determined the necessary corrections
to the polarization, and single-photon transmissions, used for the generation
of secret key material. The corrections themselves were applied using a set
of Pockels cells that also controlled the transmitted polarization state in a
BB84 implementation. A system of this kind [13] implemented error correc-
tion and privacy amplification in 1994, and it was the first fully automatic and
continuously operating quantum key distribution system.
Quantum key distribution systems based on an interferometric approach
are now widely used. They have the advantage of being relatively insensitive
to changes in the state of polarization in optical fibers. The evolution of in-
terferometer systems of this kind is illustrated in Figure 6.1. The two-photon
interferometer shown in Figure 6.1(a) was proposed by one of the authors
φ
1
φ
2
L
L
(a)
Source
S
S
φ
1
φ
2
L
L
(b)
Source
S
S
φ
1
Strong
φ
2
L
(c)
Source
Faraday
mirror
S
Weak
Figure 6.1
Evolution of interferometer-based quantum key distribution systems. (a)
Nonlocal interferometer suggested by Franson in which an entangled pair of photons
propagate toward two separated interferometers with a long path L and a short path S.
(b) Modification by Bennett to utilize a single photon passing through two interferom-
eters in series. (c) Plug-and-play system by Gisin's group that folds the above system
in half using a Faraday mirror.