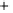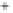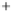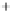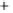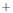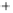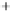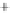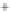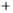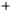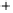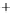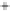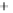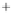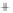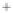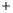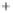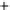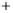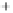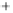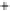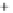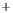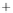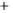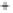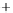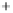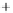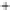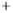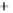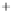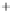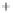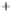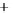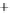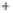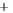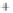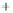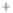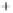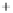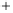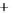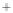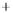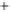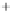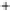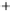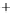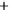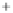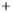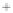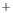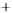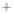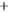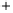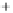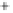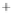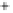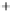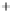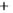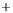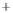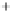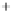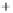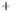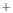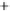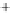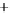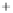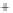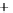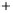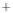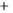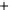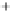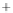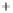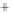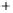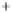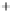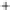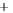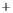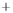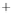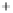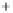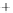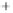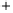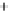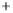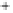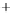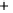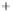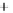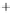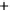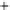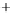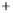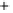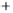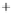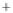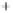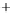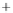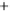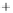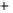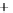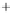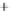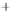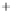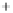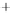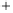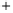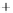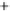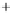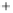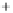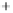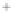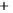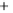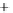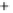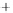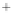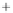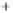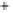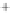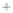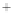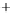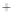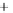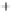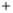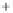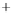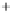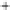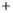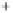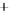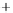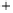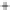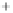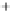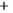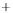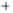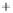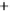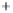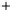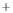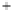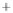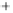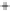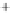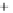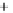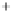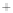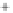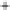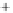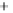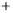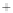Cryptography Reference
In-Depth Information
0.5
0.0
-0.5
-0.5
0.0
0.5
Figure 5.4
Plot of possible Q-function measurement results for Bob. Alice produces
four coherent states with either positive or negative
S
2
and
S
3
polarization. In the
experiment, the state overlap is high, so the states cannot be distinguished. In this
figure, the overlap is low for better visualization.
uncertainty sphere centered around
(
S
1
,
0
,
0
)
. For the sake of better visual-
ization, the coherent state with low
is shown. The modulation in
S
2
,S
3
results in moving the state around on the Poincare sphere. Modulation in
S
2
is depicted in Figure 5.3 by two further coherent states, which differ by some
angle
S
1
plane corresponding to two modulation amplitudes.
Again, for better visualization, states with low overlap between the initial
and two modulated states are shown. With growth of
θ
in the
(
S
1
,S
2
)
and increasing
overlap, the radius of the Poincare sphere goes to infinity,
S
1
can be assumed
classical, and three depicted states form in the
S
1
plane the well-known
picture of overlapping nonorthogonal states exactly as one is used for coher-
ent states in quadrature amplitude representation (see also Figure 5.4). Note
that, in contrast to the BB84, we do not deal here with two nonorthogonal
pairs of orthogonal states, all involved states are nonorthogonal. This differ-
ence will explained in greater detail in the next section and is an important
feature of our protocol.
(
S
2
,S
3
)
5.4 Protocol
The security of the BB84 relies in the first line on the nonorthogonality of the
two bases. Does one really need two nonorthogonal bases with two orthogo-
nal signal states each? Would it not suffice to exploit just a few nonorthogonal
states [6]? The answer is yes, but certain additional arrangements are required
to fix an arising security loophole, as we will describe in the following. The first
protocol of this type was the B92 protocol, which was suggested by Bennett