Cryptography Reference
In-Depth Information
Thus we update
i
,
j
, and
S
, and we output a byte which is given by
S
at index
S
[
i
]
+
S
[
j
].
2.8.3 A5/1: GSM Encryption
A5/1 is another stream cipher which is part of the A5 family. It is used in the GSM
mobile telephone networks. It is used in order to secure phone calls in the radio link
from the mobile telephone to the base station. It was designed by the SAGE group of
ETSI. The description of A5/1 is another trade secret, but the algorithm was reverse-
engineered and published in the Internet. It is commonly admitted that this description
is similar to the ETSI one.
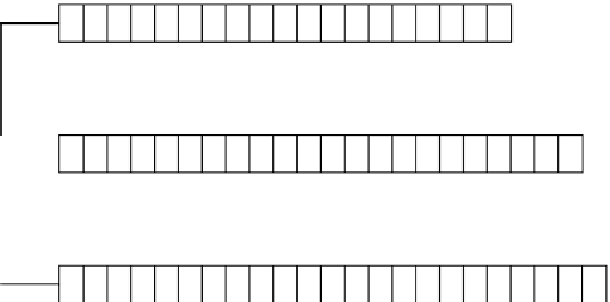
A5/1 is also based on a finite automaton with an internal state. As depicted in
Fig. 2.30, A5/1 is based on three LFSRs with a mutual clock control. The three registers
R
1
,
R
2
,
R
3
contain 19, 22, and 23 bits respectively. The internal state thus has 19
+
22
64 bits. Every time unit, some registers are clocked and some may not be
clocked at all. When a register is clocked, it means that its content is shifted by one
bit position and that a new bit is pushed. This new bit is the XOR of a few bits of the
involved LFSRs.
+
23
=
More precisely,
R
1
has 19 bits
R
1
[0]
,...,
R
1
[18]. When
R
1
is clocked, the content
R
1
[0]
,...,
R
1
[18] is replaced by
b
,
R
1
[0]
,...,
R
1
[17], i.e.
R
1
is shifted by inserting a
new bit
b
which is computed by
b
=
R
1
[13]
⊕
R
1
[16]
⊕
R
1
[17]
⊕
R
1
[18]
.
R
2
has 22 bits
R
2
[0]
,...,
R
2
[21]. When
R
2
is clocked, it is similarly shifted by inserting
a new bit
×
⊕ ⊕
⊕
⊕
×
⊕
×
⊕ ⊕
⊕
Figure 2.30.
A5/1 automaton.










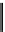





Search WWH ::

Custom Search