Cryptography Reference
In-Depth Information
K
1
⊕
F
K
2
⊕
F
K
3
⊕
F
Figure 2.2.
Function
(
F
K
1
,
F
K
2
,
F
K
3
).
is XORed to the other part. We obtain two parts which are then exchanged (except in
the final round). The round function uses subkeys derived from a secret key.
This elementary process is iterated, and the number of round function applications
is called the number of rounds. We usually denote
F
r
) the permutation ob-
tained from an
r
-round Feistel scheme in which the round functions are
F
1
,...,
(
F
1
,...,
F
r
. All
F
i
may come from a single function
F
with a parameter
K
i
defined by a subkey. We de-
note
F
i
=
F
K
i
. Fig. 2.2 illustrates a 3-round Feistel scheme. DES consists of 16 rounds.
More precisely, DES starts by a bit permutation IP, performs the Feistel cipher
using subkeys generated by a key schedule, and finally performs the inverse of the IP
permutation. This is illustrated in Fig. 2.3.
X
K
IP
K
1
K
2
Feistel
Schedule
K
16
IP
−
1
Y
Figure 2.3.
DES architecture.











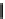

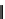

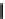








Search WWH ::

Custom Search