Cryptography Reference
In-Depth Information
0
→
1
→
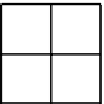
Figure 1.2.
Pixel coding for visual cryptography.
whose XOR is 0. Hence we can visually decrypt. As an example, Fig. 1.4 shows a
ciphertext, a key, and what we see from the overlay.
1.1.5 Enigma: Toward Industrial Cryptography
A famous example of an industrial encryption scheme is the Enigma machine which
was used by the Germans during World War II.
We let
π
be a fixed permutation over the 26-character alphabet with the following
properties:
it has no fixed point (
π
(
x
)
=
x
for any
x
),
it is an involution (
π
(
π
(
x
))
=
x
for any
x
).
We let
S
be a set of five permutations over the alphabet. For
α
∈
S
,welet
α
i
denote
ρ
−
i
i
i
◦
α
◦
ρ
where
ρ
is the circular rotation over the alphabet by one position (
ρ
thus denotes the circular rotation over the alphabet by
i
positions). We let
be any
involution over the alphabet with the property that it has exactly six fixed points. We
pick
σ
α, β, γ
∈
S
pairwise different. We pick a number
a
.
0
⊕
0
−→
≈
0
⊕
1
−→
=
−→
=
1
⊕
0
−→
≈
1
⊕
1
Figure 1.3.
Visual pixel XOR.












Search WWH ::

Custom Search