Cryptography Reference
In-Depth Information
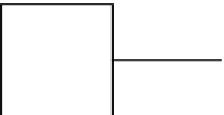
Enc
Ciphertexts
Plaintexts
Adversary
K
Figure 4.1.
Chosen plaintext attack.
Let
f
be the five first rounds of DES and let us define
a
and
b
in hexadecimal by
a
=
405c0000 04000000
,
b
=
04000000 405c0000
The following heuristic analysis suggests that
DP
f
(
a
2
−
13
.
4
,
b
)
≈
which we summarize by
f
−−−−−−−−−→
DP
.
405c0000 04000000
04000000 405c0000
≈
2
−
13
.
4
In order to trace how this difference propagates throughout the DES design, we will
analyze the
S
-boxes input and output differences. Hexadecimal notations are convenient
for the 64-bit blocks. However, since S-boxes have inputs of 6 bits, it is more convenient
to represent the 48-bit input differences in octal: any two consecutive octal digits
represent the input of a single S-box.
Assuming that the input difference of the right half of the first round is
04000000
in hexadecimal, this corresponds to the input of the first round function. After the
expansion, the difference is
00 10 00 00 00 00 00 00
in octal (see Fig. 4.2). This means
that the input of
S
2
is the only modified one. Next we observe that
1
4
DP
S
2
(
10
,
a
)
=
which means that an input difference of
10
in
S
2
will lead to an output difference of
a
in hexadecimal (
1010
in binary) with probability
4
. After the permutation in the
round function, we obtain an output difference of
40080000
in hexadecimal. This
means that the round function
F
of DES is such that
1
4
.
DP
F
(
04000000
,
=
40080000
)




Search WWH ::

Custom Search