Cryptography Reference
In-Depth Information
c
i
K
1
MAC
c
i
H
(
K
1
||
X
i
)
X
i
Adversary
K
1
(
H
(
K
1
||
X
)
,
c
)
(
X
,
c
)
Figure 3.14.
Adversary reduction by simulation in HMAC.
3. When
A
terminates by giving a forged (
X
,
c
) pair, we compute
H
(
K
1
||
X
). If
the result is equal to one previously computed
H
(
K
1
||
X
i
), then this provides
a collision on
H
. But this was assumed to be infeasible. Hence,
H
(
K
||
X
)is
different from all previously queried
H
(
K
1
||
X
i
), and (
H
(
K
1
||
X
)
,
c
) is thus a
forgery for the small MAC.
The simulation is depicted in Fig. 3.14.
3.4.7 An Authenticated Mode of Operation
We conclude on message authentication codes with an example of mode of operation
which combines encryption and MAC at the same time. Namely, those combined modes
of operation can be used to achieve confidential communications which need to have
strong integrity and authentication protection. They are called
authenticated modes of
operation
. Several authenticated modes of operation exist. The most popular one at this
time is called
counter with CBC-MAC
(CCM). It is designed to be used with AES or
any other block cipher which uses 128-bit blocks.
As its name suggests, the CCM mode combines the CTR mode and CBC-MAC.
Roughly speaking, the authenticated encryption of a message
m
is made by first com-
puting the raw CBC-MAC
T
of
m
, and then encrypting
T
m
in CTR mode. The attacks
that we have seen on the raw CBC-MAC are thwarted by the encryption of the output
tag.
||
More precisely, the CCM uses two parameters: the size
M
(in bytes) of the CBC-
MAC tag
T
which must be even and lie between 4 and 16, and the size
L
(in bytes) of
the field which will encode the message length, which must lie between 2 and 8. Note
that
M
and
L
are encoded using 3 bits each, namely by the binary expansion of
M
−
2
2
1 is reserved.
6
and
L
−
1 respectively. The value
L
=
6
For instance, future applications using messages whose length encoding (in bytes) requires more than 8
bytes (i.e. whose length is larger than 256
8
bytes, or 2
34
GB) may later use this value.







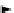
Search WWH ::

Custom Search