Database Reference
In-Depth Information
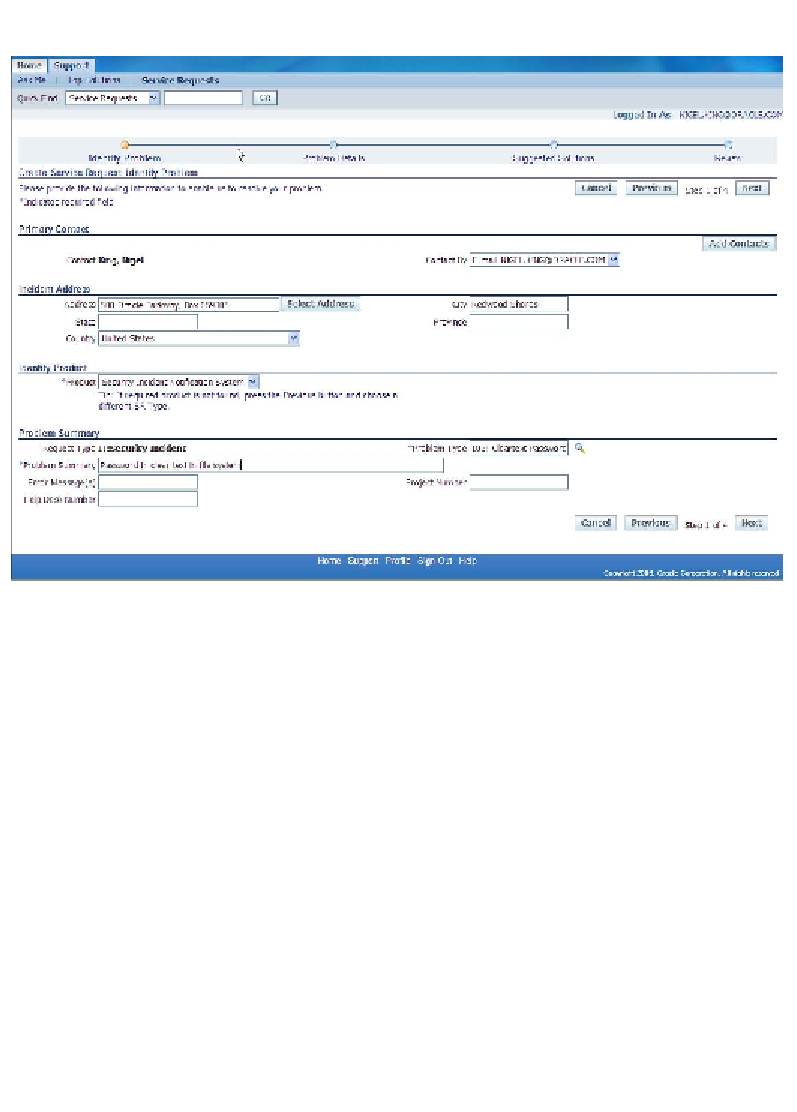
The next screenshot shows the details of a security incident being entered:
We ensure that the security incidents are also captured. We take special attention
to the configuration of the service product when capturing security incidents.
The security incidents themselves should not become a broadcast mechanism to
advertise the discovered vulnerability. There may be many alternative ways to
capture security incident with the E-Business Suite. We recommend using the Service
Request system. The service request system was designed to record service requests
for products that you sell, but it is well suited to this task with a bit of configuration.
In order to configure the service request, log in to the
applications
as an
Oracle
iSupport Administrator
. From here, you can configure the service request types,
task flows, and pages that capture the security incident information and the request
templates that guide and speed data entry for the service request. Details of how
to configure different types of service requests is explained in
Chapter 2
,
Corporate
Governance
, in the context of whistle-blower reporting.
Search WWH ::

Custom Search