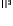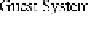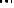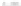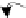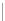Information Technology Reference
In-Depth Information
R1
S1: DNS Request; www.google.com.br; Good
R1: DNS Response; Ip addr is x.x.x.x
S2: Http; GET / HTTP/1.1; web page
R2
: 200 OK
…
S1
R2
S2
S3: DNS Request; valehoje.com.br; Bad
R3: DNS Response; Ip addr is y.y.y.y
S4: Http; GET /winjar32T.dll HTTP/1.1; download exe
R4
: 200 OK
…
R3
S3
R4
S4
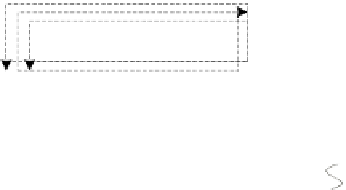
Fig. 1.
A sample of network behavior specification
In
Fig. 1,
the malware sample queries a DNS domain name
www.google.com.br
firstly, and then connects this IP address with HTTP GET request after a DNS response
packet received. And then a DNS domain name
valehoje.com.br
is queried and its
response packet is received successfully. The last domain name is malicious. The
malware launches a HTTP GET packet to download a DLL file named winjar32T.dll. It
received this binary file successfully. The
R2
and
R4
are italic notes with all packets in
a TCP session respectively. All packets are delivered immediately and the malware
sample quits its running after the network activity stopped, so we do not give the
time
information in this sample.
3
Mining NBS Based on Binary Analysis
In this section, we present the approach of mining NBS based on binary analysis,
named NBSBA. The overview of NBSBA is as shown in
Fig. 2
.
Fig. 2.
The Overview of NBSBA
The basic mining process using NBSBA is as following. The executable under
analysis is running in Guest System that is configured to communicate with the As-
sistant System. All execution activities will be recorded by Monitor System, including
all packets received from or sent to network and instructions. The
recv
and
send