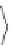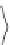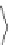Information Technology Reference
In-Depth Information
Definition 6
Access Control Policy (Semantic Definition):
Semantics of access control policy consists of semantics of access control rules. So the
semantic formal representation of access control policy is as follows:
ξ
,
ξ
,
ξ
,
INHERIT
CONTAIN
ACTION1
=
;
POLICY
ξ
,...,
ξ
ACTION 2
ACTION
n
ξ
ξ
ξ
⊆
×
;
SUBJECT
SUBJECT
INHERIT
⊆
×
;
(6)
OBJECT
OBJECT
CONTAIN
⊆
×
∪
×
;
SUBJECT
OBJECT
OBJECT
SUBJECT
ACTION
k
knn
1
≤≤
;
≥
1;
Where,
POLICY
represents the semantic of access control policy, which includes
the inheritance relationship of subject
ξ
, the relationship between objects
INHERIT
ξ
and the relationship between subject and object
,
ACTION 2
,…,
ξ
ξ
CONTAIN
ACTION1
.
The semantics between rules of access control policy is implicit, since there are
inheritance relationship and inclusion relationship between the rules. The implicit
semantics of access control policy between subjects having inheritance relationship is
expressed as axiom 1, 2 and 3.
ξ
ACTION
n
ξ
ξ
Axiom 1
Relationship of
INHERIT
,
is reflexive and transitive.
CONTAIN
Axiom 2
Semantics implied by the inheritance relationship between subjects is:
For any
subject
i
subject
j
object
k
:
1if
and
, then:
subject
,
subject
∈
subject
,
object
∈
i
j
INHERIT
j
k
ACTION
k
subject
,
object
∈
i
k
ACTION
k
2if
and
, then:
subject
,
subject
∈
object
,
subject
∈
i
j
INHERIT
k
j
ACTION
k
object
,
subject
∈
k
i
ACTION
k
Axiom 3
Semantics implied by the inclusion relationship between objects is
:
For any
subject
l
object
m
object
n
:
if
and
, then:
object
object
mn
,
∈
subject
,
object
∈
CONTAIN
l
m
ACTION
k
subject
,
object
∈
l
n
ACTION
k
2if
and
, then:
object
object
mn
,
∈
object
,
subject
∈
CONTAIN
m
l
ACTION
k
object
,
subject
∈
n
l
ACTION
k