Information Technology Reference
In-Depth Information
“bufferflow” and “dos”. Wherein, when IDS1 detects the attacks including
“bufferflow” and “dos”, IDS1 sends information to the vulnerability server where the
distributed vulnerabilities detection software is installed. The vulnerability server is
informed of vulnerability CVE-2002-0509 and CVE-2002-0037 and it sends alert
information subsequently. Then, the firewall interface of IP 192.168.1.5 will add a
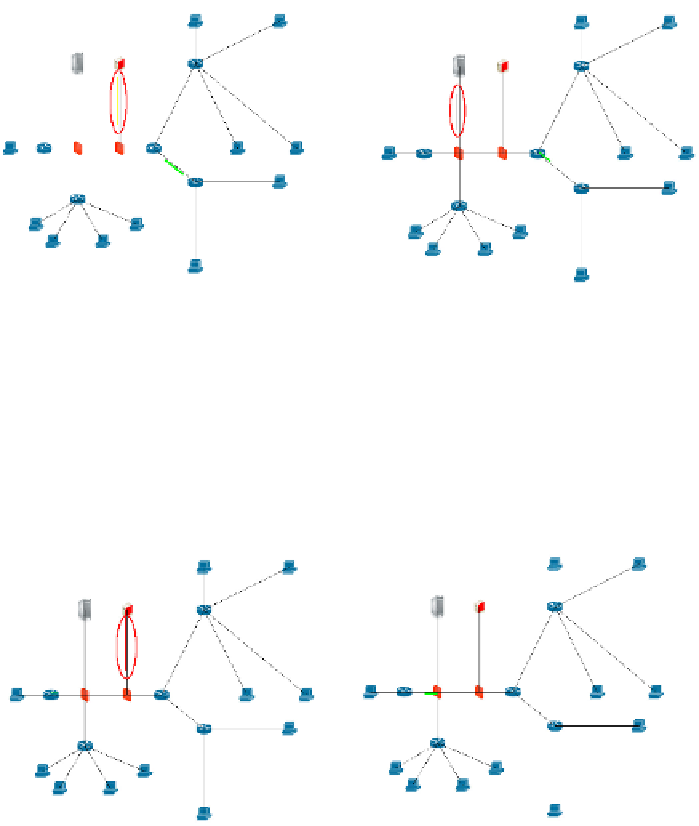
denying rule. The running effectiveness in simulation platform GTNetS is shown in the
Fig.2. The yellow packet in the circle denotes enquiring packet from IDS to
vulnerability library.
The vulnerability server queries the database and affirms this attack. Then it sends
affirmed information to IDS. In Fig. 3, the gray packet in the circle denotes affirmed
packet from vulnerability library to IDS.
Fig. 2.
Inquiring message
Fig. 3.
Affirming message
In Fig. 4, the red packet in the circle denotes that IDS informs the firewall1 to forbid
the unlawful access after receiving the vulnerability affirmed information.
In this way, the packet of attacker cannot bypass the firewall1. It is shown in Fig. 5.
The control platform results of the packet denying from attacker are shown in Fig. 6.
Based on this experiment, we find that IDS, Firewall, and vulnerability server
execute policy correctly. When there is some vulnerability in the network, the linkage
of security equipment can complete network defense effectively. And there is no need
for human interference.
Fig. 4.
Denying packet message
Fig. 5.
The packet denied from attacker