Information Technology Reference
In-Depth Information
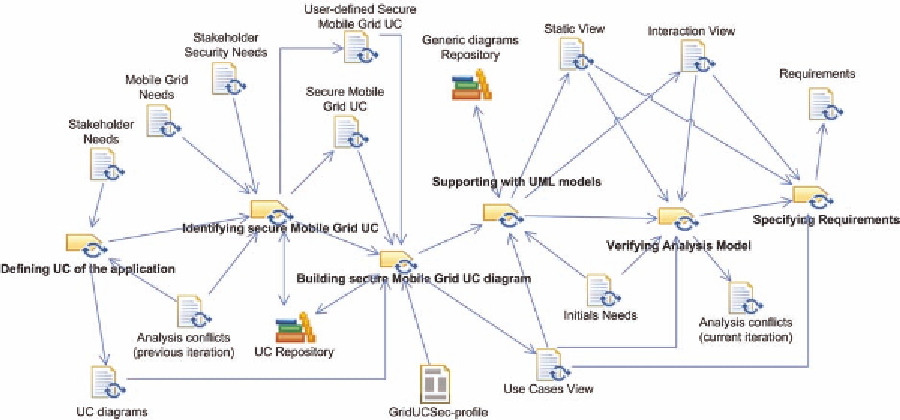
Figure 2. Tasks and artifacts of the Secure Mobile Grid System Analysis activity
3.
Building secure Mobile Grid Use Cases
diagram
. Once the use cases have been
identified and defined, we build the overall
use case diagram (or diagrams) in which we
define the relationships between all the use
cases and actors previously identified, and
we describe the information from all the
diagram's elements by following a new UML
profile for Mobile Grid use cases (Rosado,
Fernández-Medina, López, & Piattini,
2011a). We can also reuse and integrate
some diagrams with common features of
the repository which have been previously
built for Mobile Grid environments.
4.
Supporting with UML models
. In this task we
complete the analysis model with different
UML models such as the sequence and col-
laboration diagrams according to use cases
and scenarios, or class diagrams for an initial
structural description of the system from the
use cases diagrams built in previous tasks.
5.
Verifying Analysis Model
. The purpose of
this task is to verify that the artifacts have
been correctly generated and the possible
conflicts or errors in the analysis model
have to be identified and analyzed for their
subsequent refinements and corrections in
next iterations of this activity.
6.
Specifying Requirements.
This task consists
of the formal definition of the requirements
identified in previous tasks (functional
requirements and non-functional require-
ments including security) in natural language
(though a template of requirements specifi-
cation will be defined in the future).
Once we have described the tasks of the analy-
sis activity, we will explain the task 2, which is in
charge of analyzing security requirements for the
mobile grid system, and we apply the steps of this
task in a case study. This task have been improved
and updated with regard to the published work in
(Rosado, Fernández-Medina et al., 2009b).
C. Task 2: Definition of secure
Mobile Grid Use Cases
In this task, a study of the system security must
be carried out before identifying the security use
cases and misuse cases of the repository. First,
Search WWH ::

Custom Search