Information Technology Reference
In-Depth Information
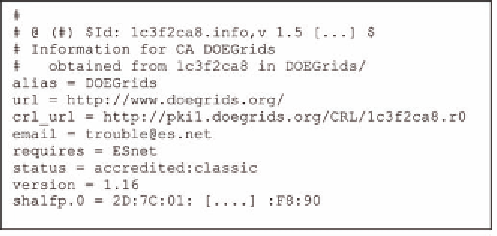
Figure 2. Example of distributed info file within grid communities. Notice how some of the distributed
information have no equivalent pointers in standard X509 certificates
revocation lists from the CRL url for
each CA
.
This means that many grid software installations
in the world are downloading these large CRLs
from the CA providers at regular intervals. From
what we have seen, this has often created denial
of service conditions for certain CAs.
The
namespaces file
defines the
Distinguished
Names (DN)
namespace that the CA is authorized
to use; the
signing policy file
defines the rules for
the signing policy of that CA. The
namespaces
file
and the
signing policy file
may contain over-
lapping information from a policy point of view
(although only the
signing policy file
has an imple-
mentation in software). Although this information
could be embedded into a CA's certificate, the
need for updating this data periodically led to the
creation of the .info file and bundling it together
with the certificate.
TACAR (Terena Academic CA Repository)
and
IGTF
register and distribute this information
to users and sites as follows. The accredited CA
sends the trust anchor information directly to the
IGTF/TACAR through a TERENA officer or a
TERENA TACAR trusted introducer.
The IGTF packages and distributes the of-
ficial CA package. Relying parties download the
IGTF package every time there is a new release
(approximately once a month). Relying parties
are encouraged to verify this against the TACAR
repository. Then, based on the information within
the downloaded package, relying parties download
the CRL from the CRL URL on a daily basis.
Ultimately, in most cases, this relies on a very
static “cron-based” process. There are several im-
provements to this that can be made by PRQP that
would replace this type of static file and crontab
based access with something more dynamic, and
query driven.
Other Solutions.
To publish pointers to data,
a CA could use certificate extensions such as
the
Authority Information Access
(AIA) and the
Subject Information Access
(SIA) (R. Housley, W.
Polk, W. Ford, and D. Solo, 2002). Regrettably
the lack of support built into applications and the
difficulties in updating extensions in certificates
clash with the need for flexibility required by
today CAs.
To overcome the problem with updating the
pointers, it is possible to use SRV records (A.
Gulbrandsen, P. Vixie, and L. Esibov, 2000) in
DNS (P. Mockapetris, 1987). Although interesting,
the problem with this solution resides in the lack
of correspondence between the DNS structure,
which is built on a strictly hierarchical namespace,
and PKIs where there are no requirements for the
used namespace.
Other solutions are either overly complicated to
solve our problem---e.g., Web Services (F. Curb-
era, M. Duftler, R. Khalaf, W. Nagy, N. Mukhi,
and S. Weerawarana, 2002) uses
SOAP
(A. Kar-
markar, M. Hadley, N. Mendolsohn, Y, Lafon, M.
Search WWH ::

Custom Search