Information Technology Reference
In-Depth Information
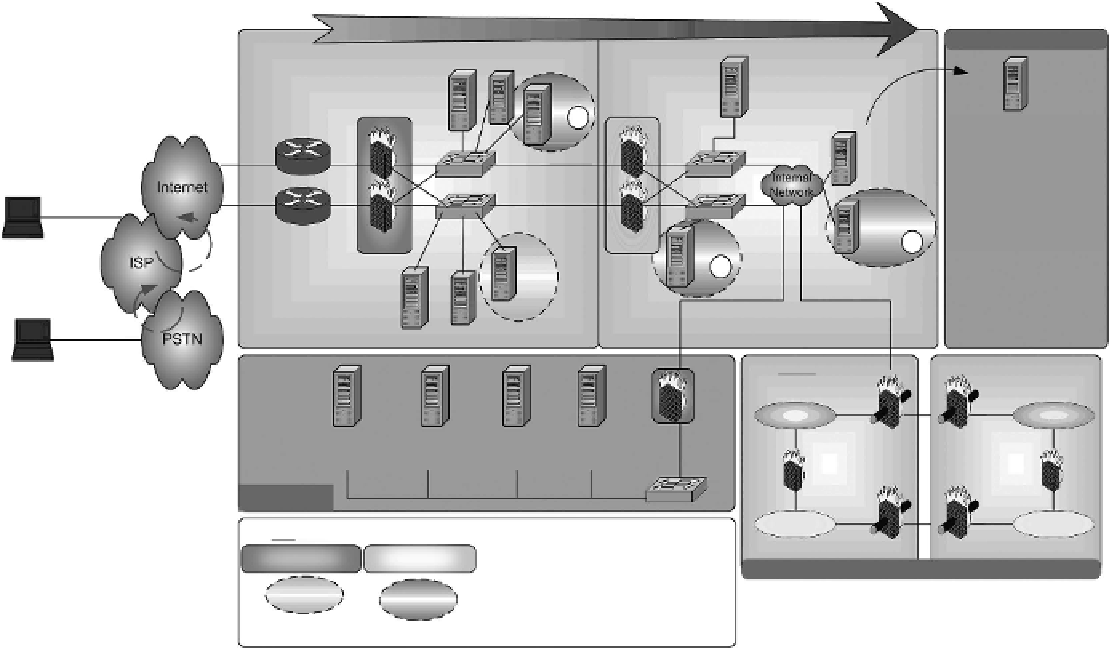
Defense-In-Depth
Host Example
Web Server(s)
Vulnerability
Assessment
Tool
Internet Traffic
Content Filtering
IDS
a
- Teleworker
- Mobile Worker
- Customer
Host Based Safeguards:
- OS Config
- Background Services
-Anti-malware
- IDS
- Logging
-Etc.
Application
Server
Database
Server
Cable/DSL
Redundant ISP
Connection
Remote
Authentication
Server
c
- IDS
b
Remote User
IDS
Dial-Up
E-mail
Real-time
Monitoring
& Alert
Anti-
virus
Site 1
Site 2
Remote User
COI
1
COI
1
SNMP
Monitor
Log Mgmt
Server
AV Server
Firewall
Mgmt
NOC/SOC
COI
2
COI
2
NOC = Network Operating Center
SOC = Security Operating Center
COI = Community of Interest
Key
VPN VPN
Intra-Organizational Network Example
Stateful Firewalls
Proxy Firewalls
IDS
Placement
a
Perimeter Network IDS
Internal Network IDS
Host-based IDS
Honeypot
b
c
Figure 9.5
iDS and honeypot in context of defense-in-depth.